| Name | CVE-2022-21500 JSON |
| Version |
0.0.1
 JSON
JSON |
| download |
| home_page | None |
| Summary | None |
| upload_time | 2024-06-17 12:27:16 |
| maintainer | None |
| docs_url | None |
| author | @karthithehacker |
| requires_python | None |
| license | None |
| keywords |
|
| VCS |
|
| bugtrack_url |
|
| requirements |
No requirements were recorded.
|
| Travis-CI |
No Travis.
|
| coveralls test coverage |
No coveralls.
|
<div align="center">
<img src="https://blogs.cappriciosec.com/uploaders/CVE-2022-21500-tool.png" alt="logo">
</div>
## Badges
[](https://choosealicense.com/licenses/mit/)



<a href="https://github.com/Cappricio-Securities/CVE-2022-21500/releases/"><img src="https://img.shields.io/github/release/Cappricio-Securities/CVE-2022-21500"></a>
[](https://twitter.com/cappricio_sec)
<p align="center">
<p align="center">
## License
[MIT](https://choosealicense.com/licenses/mit/)
## Installation
1. Install Python3 and pip [Instructions Here](https://www.python.org/downloads/) (If you can't figure this out, you shouldn't really be using this)
- Install via pip
- ```bash
pip install CVE-2022-21500
```
- Run bellow command to check
- `CVE-2022-21500 -h`
## Configurations
2. We integrated with the Telegram API to receive instant notifications for vulnerability detection.
- Telegram Notification
- ```bash
CVE-2022-21500 --chatid <YourTelegramChatID>
```
- Open your telegram and search for [`@CappricioSecuritiesTools_bot`](https://web.telegram.org/k/#@CappricioSecuritiesTools_bot) and click start
## Usages
3. This tool has multiple use cases.
- To Check Single URL
- ```bash
CVE-2022-21500 -u http://example.com
```
- To Check List of URL
- ```bash
CVE-2022-21500 -i urls.txt
```
- Save output into TXT file
- ```bash
CVE-2022-21500 -i urls.txt -o out.txt
```
- Want to Learn about [`CVE-2022-21500`](https://blogs.cappriciosec.com/blog/193/CVE-2022-21500)? Then Type Below command
- ```bash
CVE-2022-21500 -b
```
<p align="center">
<b>🚨 Disclaimer</b>
</p>
<p align="center">
<b>This tool is created for security bug identification and assistance; Cappricio Securities is not liable for any illegal use.
Use responsibly within legal and ethical boundaries. 🔐🛡️</b></p>
## Working PoC Video
[](https://asciinema.org/a/ckJJ5yhBQwWCqZegy8ygnBugX)
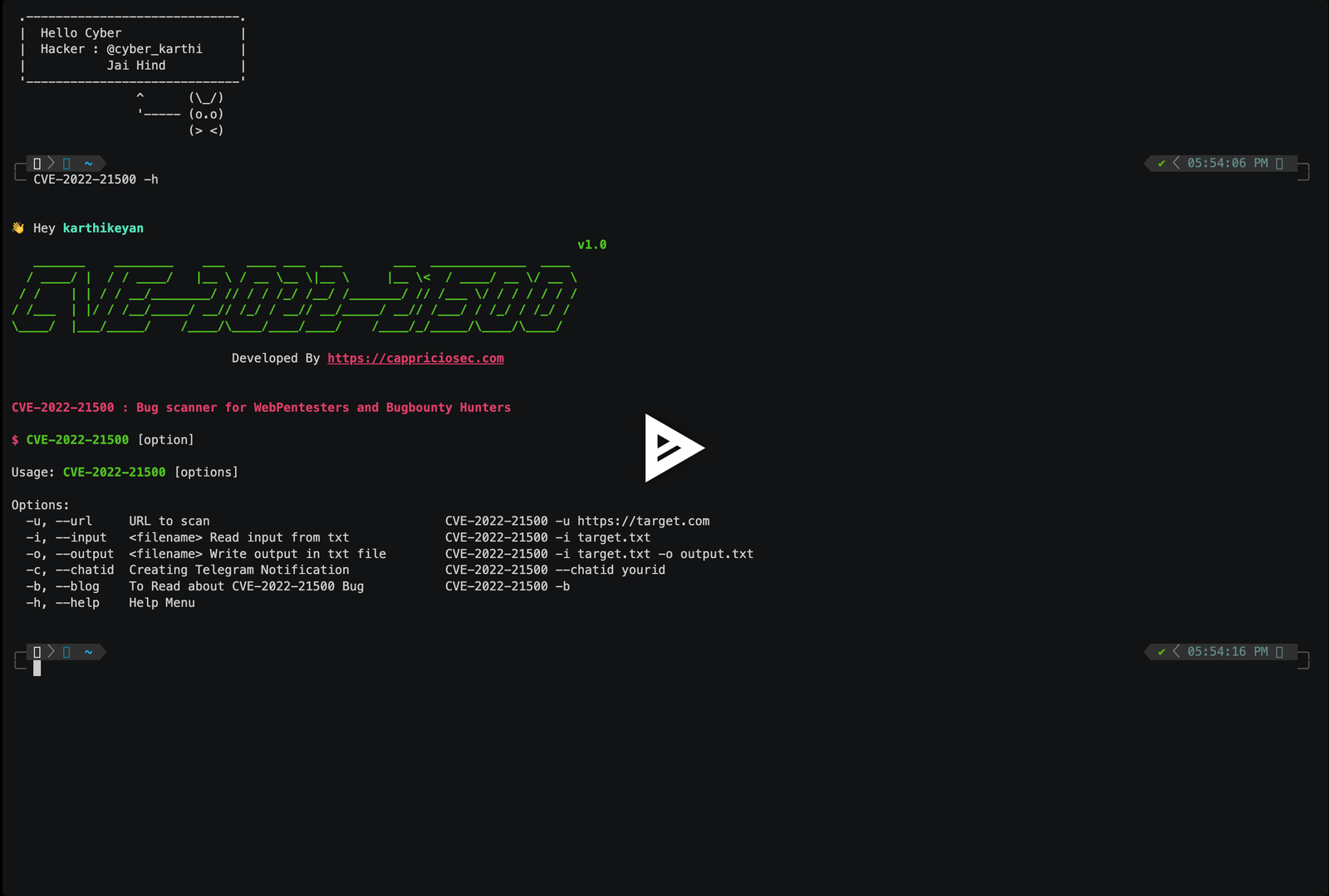
## Help menu
#### Get all items
```bash
👋 Hey Hacker
v1.0
_______ ________ ___ ____ ___ ___ ___ _____________ ____
/ ____/ | / / ____/ |__ \ / __ \__ \|__ \ |__ \< / ____/ __ \/ __ \
/ / | | / / __/________/ // / / /_/ /__/ /_______/ // /___ \/ / / / / / /
/ /___ | |/ / /__/_____/ __// /_/ / __// __/_____/ __// /___/ / /_/ / /_/ /
\____/ |___/_____/ /____/\____/____/____/ /____/_/_____/\____/\____/
Developed By https://cappriciosec.com
CVE-2022-21500 : Bug scanner for WebPentesters and Bugbounty Hunters
$ CVE-2022-21500 [option]
Usage: CVE-2022-21500 [options]
```
| Argument | Type | Description | Examples |
| :-------- | :------- | :------------------------- | :------------------------- |
| `-u` | `--url` | URL to scan | CVE-2022-21500 -u https://target.com |
| `-i` | `--input` | filename Read input from txt | CVE-2022-21500 -i target.txt |
| `-o` | `--output` | filename Write output in txt file | CVE-2022-21500 -i target.txt -o output.txt |
| `-c` | `--chatid` | Creating Telegram Notification | CVE-2022-21500 --chatid yourid |
| `-b` | `--blog` | To Read about CVE-2022-21500 Bug | CVE-2022-21500 -b |
| `-h` | `--help` | Help Menu | CVE-2022-21500 -h |
## 🔗 Links
[](https://cappriciosec.com/)
[](https://www.linkedin.com/in/karthikeyan--v/)
[](https://twitter.com/karthithehacker)
## Author
- [@karthithehacker](https://github.com/karthi-the-hacker/)
## Feedback
If you have any feedback, please reach out to us at contact@karthithehacker.com
Raw data
{
"_id": null,
"home_page": null,
"name": "CVE-2022-21500",
"maintainer": null,
"docs_url": null,
"requires_python": null,
"maintainer_email": null,
"keywords": null,
"author": "@karthithehacker",
"author_email": "<contact@karthithehacker.com>",
"download_url": "https://files.pythonhosted.org/packages/5a/25/7b825b736c58fac6e20c62f12477c220cff254b049264d0553852fd20e17/CVE-2022-21500-0.0.1.tar.gz",
"platform": null,
"description": "\n<div align=\"center\">\n <img src=\"https://blogs.cappriciosec.com/uploaders/CVE-2022-21500-tool.png\" alt=\"logo\">\n</div>\n\n\n## Badges\n\n\n\n[](https://choosealicense.com/licenses/mit/)\n\n\n\n<a href=\"https://github.com/Cappricio-Securities/CVE-2022-21500/releases/\"><img src=\"https://img.shields.io/github/release/Cappricio-Securities/CVE-2022-21500\"></a>\n[](https://twitter.com/cappricio_sec)\n<p align=\"center\">\n\n<p align=\"center\">\n\n\n\n\n\n\n\n## License\n\n[MIT](https://choosealicense.com/licenses/mit/)\n\n\n\n## Installation \n\n1. Install Python3 and pip [Instructions Here](https://www.python.org/downloads/) (If you can't figure this out, you shouldn't really be using this)\n\n - Install via pip\n - ```bash\n pip install CVE-2022-21500 \n ```\n - Run bellow command to check\n - `CVE-2022-21500 -h`\n\n## Configurations \n2. We integrated with the Telegram API to receive instant notifications for vulnerability detection.\n \n - Telegram Notification\n - ```bash\n CVE-2022-21500 --chatid <YourTelegramChatID>\n ```\n - Open your telegram and search for [`@CappricioSecuritiesTools_bot`](https://web.telegram.org/k/#@CappricioSecuritiesTools_bot) and click start\n\n## Usages \n3. This tool has multiple use cases.\n \n - To Check Single URL\n - ```bash\n CVE-2022-21500 -u http://example.com \n ```\n - To Check List of URL \n - ```bash\n CVE-2022-21500 -i urls.txt \n ```\n - Save output into TXT file\n - ```bash\n CVE-2022-21500 -i urls.txt -o out.txt\n ```\n - Want to Learn about [`CVE-2022-21500`](https://blogs.cappriciosec.com/blog/193/CVE-2022-21500)? Then Type Below command\n - ```bash\n CVE-2022-21500 -b\n ```\n \n<p align=\"center\">\n <b>\ud83d\udea8 Disclaimer</b>\n \n</p>\n<p align=\"center\">\n<b>This tool is created for security bug identification and assistance; Cappricio Securities is not liable for any illegal use. \n Use responsibly within legal and ethical boundaries. \ud83d\udd10\ud83d\udee1\ufe0f</b></p>\n\n\n## Working PoC Video\n\n[](https://asciinema.org/a/ckJJ5yhBQwWCqZegy8ygnBugX)\n\n\n## Help menu\n\n#### Get all items\n\n```bash\n\n\ud83d\udc4b Hey Hacker\n v1.0\n _______ ________ ___ ____ ___ ___ ___ _____________ ____ \n / ____/ | / / ____/ |__ \\ / __ \\__ \\|__ \\ |__ \\< / ____/ __ \\/ __ \\ \n / / | | / / __/________/ // / / /_/ /__/ /_______/ // /___ \\/ / / / / / / \n/ /___ | |/ / /__/_____/ __// /_/ / __// __/_____/ __// /___/ / /_/ / /_/ / \n\\____/ |___/_____/ /____/\\____/____/____/ /____/_/_____/\\____/\\____/\n\n Developed By https://cappriciosec.com\n\n\nCVE-2022-21500 : Bug scanner for WebPentesters and Bugbounty Hunters\n\n$ CVE-2022-21500 [option]\n\nUsage: CVE-2022-21500 [options]\n```\n\n\n| Argument | Type | Description | Examples |\n| :-------- | :------- | :------------------------- | :------------------------- |\n| `-u` | `--url` | URL to scan | CVE-2022-21500 -u https://target.com |\n| `-i` | `--input` | filename Read input from txt | CVE-2022-21500 -i target.txt | \n| `-o` | `--output` | filename Write output in txt file | CVE-2022-21500 -i target.txt -o output.txt |\n| `-c` | `--chatid` | Creating Telegram Notification | CVE-2022-21500 --chatid yourid |\n| `-b` | `--blog` | To Read about CVE-2022-21500 Bug | CVE-2022-21500 -b |\n| `-h` | `--help` | Help Menu | CVE-2022-21500 -h |\n\n\n\n## \ud83d\udd17 Links\n[](https://cappriciosec.com/)\n[](https://www.linkedin.com/in/karthikeyan--v/)\n[](https://twitter.com/karthithehacker)\n\n\n\n## Author\n\n- [@karthithehacker](https://github.com/karthi-the-hacker/)\n\n\n\n## Feedback\n\nIf you have any feedback, please reach out to us at contact@karthithehacker.com\n",
"bugtrack_url": null,
"license": null,
"summary": null,
"version": "0.0.1",
"project_urls": null,
"split_keywords": [],
"urls": [
{
"comment_text": "",
"digests": {
"blake2b_256": "5a257b825b736c58fac6e20c62f12477c220cff254b049264d0553852fd20e17",
"md5": "a0ebf4a777ceb8571faec9a0c02ddb73",
"sha256": "d198a8673fb5311760cdcdb3a362b7d7e041d7477433c8ab5b7e3bc44c9f8af8"
},
"downloads": -1,
"filename": "CVE-2022-21500-0.0.1.tar.gz",
"has_sig": false,
"md5_digest": "a0ebf4a777ceb8571faec9a0c02ddb73",
"packagetype": "sdist",
"python_version": "source",
"requires_python": null,
"size": 7794,
"upload_time": "2024-06-17T12:27:16",
"upload_time_iso_8601": "2024-06-17T12:27:16.903313Z",
"url": "https://files.pythonhosted.org/packages/5a/25/7b825b736c58fac6e20c62f12477c220cff254b049264d0553852fd20e17/CVE-2022-21500-0.0.1.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2024-06-17 12:27:16",
"github": false,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"lcname": "cve-2022-21500"
}