# 🔐 OpenVPN Client Portal
[](https://www.python.org/downloads/) [](https://flask.palletsprojects.com/) [](https://opensource.org/licenses/MIT) [](https://codecov.io/gh/ranson21/gcp-ovpn-portal)
A secure, user-friendly authentication portal for OpenVPN configuration distribution. This application provides Google OAuth2 authentication and domain-restricted access to OpenVPN configuration files.
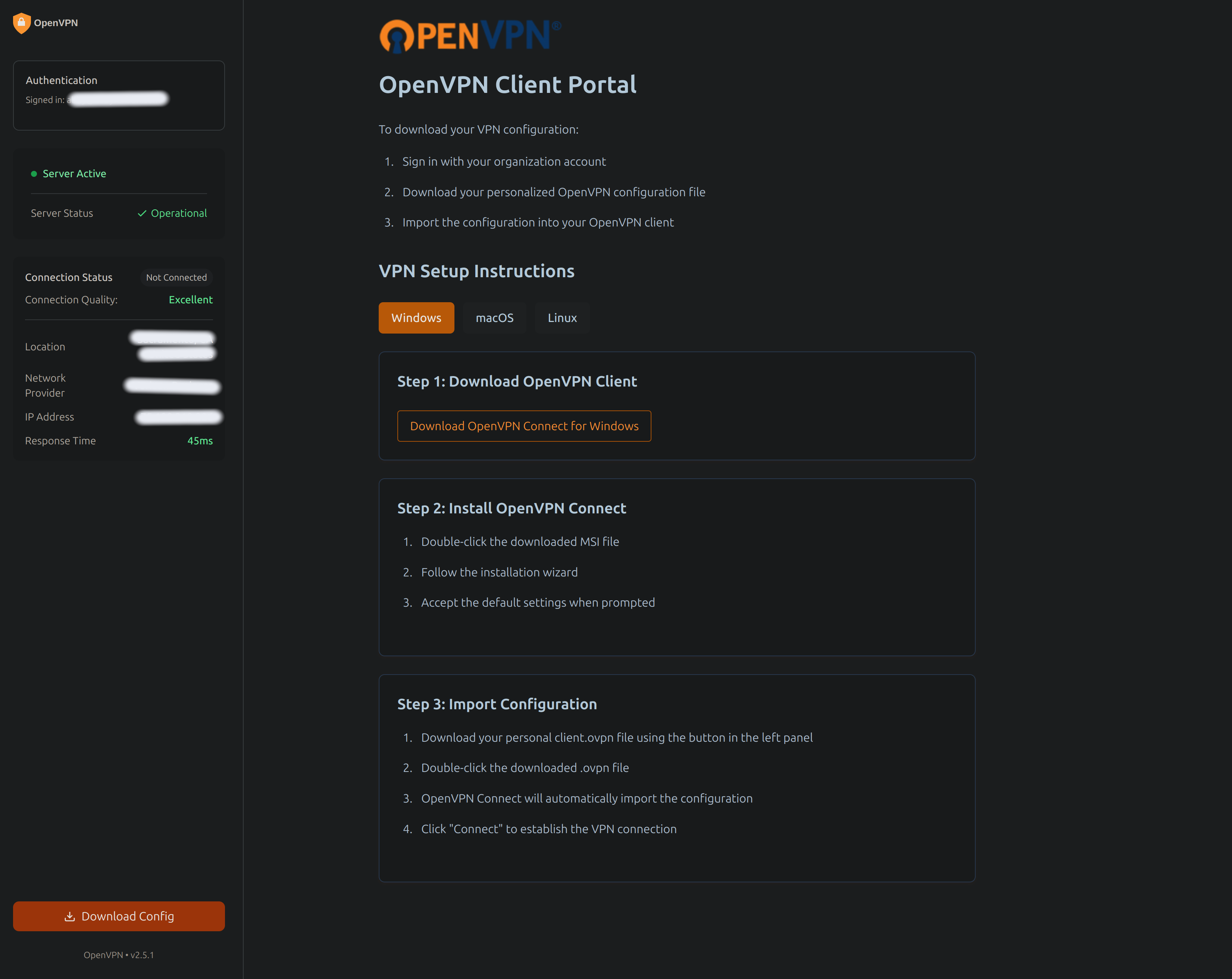
## 🌟 Features
- 🔒 Secure Google OAuth2 authentication
- 👥 Domain-restricted access control
- 📦 Automated OpenVPN config generation
- 🎨 Clean, responsive web interface
- 🚀 Easy deployment and configuration
## 📦 Installation
### Via pip
```bash
pip install gcp-ovpn-portal
```
### Development Setup
1. Clone the repository:
```bash
git clone https://github.com/ranson21/gcp-ovpn-portal
cd gcp-ovpn-portal
```
2. Install with Poetry:
```bash
poetry install
```
## 🔧 Configuration
### Google OAuth2 Setup
1. Go to the [Google Cloud Console](https://console.cloud.google.com/)
2. Create a new project or select an existing one
3. Enable the Google OAuth2 API:
- Go to "APIs & Services" > "Library"
- Search for "Google OAuth2"
- Click "Enable"
4. Configure the OAuth consent screen:
- Go to "APIs & Services" > "OAuth consent screen"
- Choose "Internal" if using Google Workspace, or "External" if not
- Fill in the application name and other required fields
- Add the necessary scopes (email, profile)
5. Create OAuth 2.0 credentials:
- Go to "APIs & Services" > "Credentials"
- Click "Create Credentials" > "OAuth client ID"
- Choose "Web application"
- Add authorized redirect URIs:
- For local development: `http://localhost:8081`
- For production: `https://your-domain.com`
- Save your Client ID and Client Secret
### Environment Variables
The following environment variables are required:
- `CLIENT_ID`: Google OAuth2 client ID (obtained from steps above)
- `ALLOWED_DOMAIN`: Authorized email domain (e.g., "company.com")
- `EXTERNAL_IP`: VPN server's external IP address
- `OPENVPN_DIR`: Directory containing OpenVPN configuration files (default: /etc/openvpn)
Create a .env file:
```bash
cp .env.example .env
# Edit .env with your configuration
```
Example .env file:
```
CLIENT_ID=your-google-client-id.apps.googleusercontent.com
ALLOWED_DOMAIN=yourcompany.com
EXTERNAL_IP=203.0.113.1
OPENVPN_DIR=/etc/openvpn
```
## 🚀 Usage
### Running as an installed package
```bash
# Run the VPN portal
ovpn-portal
```
### Running in development mode
```bash
# Using Poetry
poetry run ovpn-portal
# Or using make
make run
```
## 📁 Project Structure
```
openvpn-auth-portal/
├── ovpn_portal/
│ ├── app/
│ │ ├── main/
| │ │ ├── __init__.py
| │ │ └── routes.py
│ │ ├── __init__.py
│ │ ├── config.py
│ │ ├── middleware.py
│ │ └── vpn.py
│ └── run.py
├── static/
│ ├── css/
│ ├── images/
│ ├── js/
│ └── favicon.ico
├── templates/
│ └── index.html
├── tests/
├── pyproject.toml
├── .env.example
├── .gitignore
└── README.md
```
## 🛠️ Development
The project includes a Makefile to help with common development tasks:
### First Time Setup
```bash
make dev-setup # Install Poetry, initialize git, and install dependencies
```
### Common Commands
```bash
make install # Install project dependencies
make run # Run development server
make test # Run test suite
make coverage # Run tests with coverage report
make format # Format code with black and isort
make lint # Run linting checks
make clean # Clean temporary files and builds
```
### Test Coverage
To run tests with coverage reporting:
```bash
make coverage
```
This will:
- Run all tests with coverage tracking
- Generate a terminal report showing missing lines
- Create an HTML coverage report in `coverage_html/`
View the HTML coverage report:
```bash
make coverage-open # On macOS
# Or open coverage_html/index.html in your browser
```
### Package Management
```bash
make build # Build package distribution
make develop # Install package locally in editable mode
```
### Publishing
```bash
make publish-test # Publish to Test PyPI
make publish # Publish to PyPI
```
You can also use Poetry directly for development tasks:
```bash
poetry install # Install dependencies
poetry run pytest # Run tests
poetry run black . # Format code
poetry run flake8 # Lint code
```
## 🔒 Security Considerations
- All authentication is performed through Google OAuth2
- Configuration files are generated temporarily and immediately deleted after download
- Domain restriction ensures only authorized users can access the portal
- HTTPS is required in production
## 📄 License
This project is licensed under the MIT License - see the [LICENSE](LICENSE) file for details.
## 🤝 Contributing
Contributions are welcome! Please feel free to submit a Pull Request.
## 👤 Author
Abigail Ranson
- Website: [abbyranson.com](https://abbyranson.com)
- GitHub: [@ranson21](https://github.com/ranson21)
Raw data
{
"_id": null,
"home_page": "https://github.com/ranson21/ovpn-client-web",
"name": "gcp-ovpn-portal",
"maintainer": null,
"docs_url": null,
"requires_python": "<4.0,>=3.8.1",
"maintainer_email": null,
"keywords": "vpn, openvpn, oauth, google-auth, flask",
"author": "Abigail Ranson",
"author_email": "abby@abbyranson.com",
"download_url": "https://files.pythonhosted.org/packages/c6/80/faf3c037943d75755eb4d25239e782e616c3af828ac1b9e4666ca1008978/gcp_ovpn_portal-0.4.7.tar.gz",
"platform": null,
"description": "# \ud83d\udd10 OpenVPN Client Portal\n\n[](https://www.python.org/downloads/) [](https://flask.palletsprojects.com/) [](https://opensource.org/licenses/MIT) [](https://codecov.io/gh/ranson21/gcp-ovpn-portal)\n\nA secure, user-friendly authentication portal for OpenVPN configuration distribution. This application provides Google OAuth2 authentication and domain-restricted access to OpenVPN configuration files.\n\n\n\n## \ud83c\udf1f Features\n\n- \ud83d\udd12 Secure Google OAuth2 authentication\n- \ud83d\udc65 Domain-restricted access control\n- \ud83d\udce6 Automated OpenVPN config generation\n- \ud83c\udfa8 Clean, responsive web interface\n- \ud83d\ude80 Easy deployment and configuration\n\n## \ud83d\udce6 Installation\n\n### Via pip\n\n```bash\npip install gcp-ovpn-portal\n```\n\n### Development Setup\n\n1. Clone the repository:\n```bash\ngit clone https://github.com/ranson21/gcp-ovpn-portal\ncd gcp-ovpn-portal\n```\n\n2. Install with Poetry:\n```bash\npoetry install\n```\n\n## \ud83d\udd27 Configuration\n\n### Google OAuth2 Setup\n\n1. Go to the [Google Cloud Console](https://console.cloud.google.com/)\n2. Create a new project or select an existing one\n3. Enable the Google OAuth2 API:\n - Go to \"APIs & Services\" > \"Library\"\n - Search for \"Google OAuth2\"\n - Click \"Enable\"\n4. Configure the OAuth consent screen:\n - Go to \"APIs & Services\" > \"OAuth consent screen\"\n - Choose \"Internal\" if using Google Workspace, or \"External\" if not\n - Fill in the application name and other required fields\n - Add the necessary scopes (email, profile)\n5. Create OAuth 2.0 credentials:\n - Go to \"APIs & Services\" > \"Credentials\"\n - Click \"Create Credentials\" > \"OAuth client ID\"\n - Choose \"Web application\"\n - Add authorized redirect URIs:\n - For local development: `http://localhost:8081`\n - For production: `https://your-domain.com`\n - Save your Client ID and Client Secret\n\n### Environment Variables\n\nThe following environment variables are required:\n\n- `CLIENT_ID`: Google OAuth2 client ID (obtained from steps above)\n- `ALLOWED_DOMAIN`: Authorized email domain (e.g., \"company.com\")\n- `EXTERNAL_IP`: VPN server's external IP address\n- `OPENVPN_DIR`: Directory containing OpenVPN configuration files (default: /etc/openvpn)\n\nCreate a .env file:\n```bash\ncp .env.example .env\n# Edit .env with your configuration\n```\n\nExample .env file:\n```\nCLIENT_ID=your-google-client-id.apps.googleusercontent.com\nALLOWED_DOMAIN=yourcompany.com\nEXTERNAL_IP=203.0.113.1\nOPENVPN_DIR=/etc/openvpn\n```\n\n## \ud83d\ude80 Usage\n\n### Running as an installed package\n\n```bash\n# Run the VPN portal\novpn-portal\n```\n\n### Running in development mode\n\n```bash\n# Using Poetry\npoetry run ovpn-portal\n\n# Or using make\nmake run\n```\n\n## \ud83d\udcc1 Project Structure\n\n```\nopenvpn-auth-portal/\n\u251c\u2500\u2500 ovpn_portal/\n\u2502 \u251c\u2500\u2500 app/\n\u2502 \u2502 \u251c\u2500\u2500 main/\n| \u2502 \u2502 \u251c\u2500\u2500 __init__.py\n| \u2502 \u2502 \u2514\u2500\u2500 routes.py\n\u2502 \u2502 \u251c\u2500\u2500 __init__.py\n\u2502 \u2502 \u251c\u2500\u2500 config.py\n\u2502 \u2502 \u251c\u2500\u2500 middleware.py\n\u2502 \u2502 \u2514\u2500\u2500 vpn.py\n\u2502 \u2514\u2500\u2500 run.py\n\u251c\u2500\u2500 static/\n\u2502 \u251c\u2500\u2500 css/\n\u2502 \u251c\u2500\u2500 images/\n\u2502 \u251c\u2500\u2500 js/\n\u2502 \u2514\u2500\u2500 favicon.ico\n\u251c\u2500\u2500 templates/\n\u2502 \u2514\u2500\u2500 index.html\n\u251c\u2500\u2500 tests/\n\u251c\u2500\u2500 pyproject.toml\n\u251c\u2500\u2500 .env.example\n\u251c\u2500\u2500 .gitignore\n\u2514\u2500\u2500 README.md\n```\n\n## \ud83d\udee0\ufe0f Development\n\nThe project includes a Makefile to help with common development tasks:\n\n### First Time Setup\n```bash\nmake dev-setup # Install Poetry, initialize git, and install dependencies\n```\n\n### Common Commands\n```bash\nmake install # Install project dependencies\nmake run # Run development server\nmake test # Run test suite\nmake coverage # Run tests with coverage report\nmake format # Format code with black and isort\nmake lint # Run linting checks\nmake clean # Clean temporary files and builds\n```\n\n### Test Coverage\n\nTo run tests with coverage reporting:\n```bash\nmake coverage\n```\n\nThis will:\n- Run all tests with coverage tracking\n- Generate a terminal report showing missing lines\n- Create an HTML coverage report in `coverage_html/`\n\nView the HTML coverage report:\n```bash\nmake coverage-open # On macOS\n# Or open coverage_html/index.html in your browser\n```\n\n### Package Management\n```bash\nmake build # Build package distribution\nmake develop # Install package locally in editable mode\n```\n\n### Publishing\n```bash\nmake publish-test # Publish to Test PyPI\nmake publish # Publish to PyPI\n```\n\nYou can also use Poetry directly for development tasks:\n```bash\npoetry install # Install dependencies\npoetry run pytest # Run tests\npoetry run black . # Format code\npoetry run flake8 # Lint code\n```\n\n## \ud83d\udd12 Security Considerations\n\n- All authentication is performed through Google OAuth2\n- Configuration files are generated temporarily and immediately deleted after download\n- Domain restriction ensures only authorized users can access the portal\n- HTTPS is required in production\n\n## \ud83d\udcc4 License\n\nThis project is licensed under the MIT License - see the [LICENSE](LICENSE) file for details.\n\n## \ud83e\udd1d Contributing\n\nContributions are welcome! Please feel free to submit a Pull Request.\n\n## \ud83d\udc64 Author\n\nAbigail Ranson\n- Website: [abbyranson.com](https://abbyranson.com)\n- GitHub: [@ranson21](https://github.com/ranson21)",
"bugtrack_url": null,
"license": "MIT",
"summary": "A secure OpenVPN authentication portal with Google OAuth2",
"version": "0.4.7",
"project_urls": {
"Documentation": "https://github.com/ranson21/ovpn-client-web#readme",
"Homepage": "https://github.com/ranson21/ovpn-client-web",
"Repository": "https://github.com/ranson21/ovpn-client-web"
},
"split_keywords": [
"vpn",
" openvpn",
" oauth",
" google-auth",
" flask"
],
"urls": [
{
"comment_text": "",
"digests": {
"blake2b_256": "8f8868b2303425ea26fb06ee6fec52692c4a5a6418e9443cfa8af5e5ca55d265",
"md5": "3f650e59c37ed9bcff6697c24e9d8731",
"sha256": "b5a675b5ff66b4e4a80ed2aa139b3127d7d802341a0de5fa7637ceb29e3f6451"
},
"downloads": -1,
"filename": "gcp_ovpn_portal-0.4.7-py3-none-any.whl",
"has_sig": false,
"md5_digest": "3f650e59c37ed9bcff6697c24e9d8731",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": "<4.0,>=3.8.1",
"size": 155871,
"upload_time": "2025-01-15T20:55:41",
"upload_time_iso_8601": "2025-01-15T20:55:41.876766Z",
"url": "https://files.pythonhosted.org/packages/8f/88/68b2303425ea26fb06ee6fec52692c4a5a6418e9443cfa8af5e5ca55d265/gcp_ovpn_portal-0.4.7-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": "",
"digests": {
"blake2b_256": "c680faf3c037943d75755eb4d25239e782e616c3af828ac1b9e4666ca1008978",
"md5": "06bd0489d0d90ed3387a7644993e083f",
"sha256": "df577132c0292dafc9f098fd737675589593ef1329e064370598730e58d4ccc1"
},
"downloads": -1,
"filename": "gcp_ovpn_portal-0.4.7.tar.gz",
"has_sig": false,
"md5_digest": "06bd0489d0d90ed3387a7644993e083f",
"packagetype": "sdist",
"python_version": "source",
"requires_python": "<4.0,>=3.8.1",
"size": 142700,
"upload_time": "2025-01-15T20:55:43",
"upload_time_iso_8601": "2025-01-15T20:55:43.097667Z",
"url": "https://files.pythonhosted.org/packages/c6/80/faf3c037943d75755eb4d25239e782e616c3af828ac1b9e4666ca1008978/gcp_ovpn_portal-0.4.7.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2025-01-15 20:55:43",
"github": true,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"github_user": "ranson21",
"github_project": "ovpn-client-web",
"travis_ci": false,
"coveralls": false,
"github_actions": true,
"lcname": "gcp-ovpn-portal"
}
