| Name | msal JSON |
| Version |
1.33.0
 JSON
JSON |
| download |
| home_page | https://github.com/AzureAD/microsoft-authentication-library-for-python |
| Summary | The Microsoft Authentication Library (MSAL) for Python library enables your app to access the Microsoft Cloud by supporting authentication of users with Microsoft Azure Active Directory accounts (AAD) and Microsoft Accounts (MSA) using industry standard OAuth2 and OpenID Connect. |
| upload_time | 2025-07-22 19:36:33 |
| maintainer | None |
| docs_url | None |
| author | Microsoft Corporation |
| requires_python | >=3.7 |
| license | MIT |
| keywords |
|
| VCS |
 |
| bugtrack_url |
|
| requirements |
No requirements were recorded.
|
| Travis-CI |
No Travis.
|
| coveralls test coverage |
No coveralls.
|
# Microsoft Authentication Library (MSAL) for Python
| `dev` branch | Reference Docs | # of Downloads per different platforms | # of Downloads per recent MSAL versions | Benchmark Diagram |
|:------------:|:--------------:|:--------------------------------------:|:---------------------------------------:|:-----------------:|
[](https://github.com/AzureAD/microsoft-authentication-library-for-python/actions) | [](https://msal-python.readthedocs.io/en/latest/?badge=latest) | [](https://pypistats.org/packages/msal) | [](https://pepy.tech/project/msal) | [📉](https://azuread.github.io/microsoft-authentication-library-for-python/dev/bench/)
The Microsoft Authentication Library for Python enables applications to integrate with the [Microsoft identity platform](https://aka.ms/aaddevv2). It allows you to sign in users or apps with Microsoft identities ([Microsoft Entra ID](https://www.microsoft.com/security/business/identity-access/microsoft-entra-id), [External identities](https://www.microsoft.com/security/business/identity-access/microsoft-entra-external-id), [Microsoft Accounts](https://account.microsoft.com) and [Azure AD B2C](https://azure.microsoft.com/services/active-directory-b2c/) accounts) and obtain tokens to call Microsoft APIs such as [Microsoft Graph](https://graph.microsoft.io/) or your own APIs registered with the Microsoft identity platform. It is built using industry standard OAuth2 and OpenID Connect protocols
Not sure whether this is the SDK you are looking for your app? There are other Microsoft Identity SDKs
[here](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Microsoft-Authentication-Client-Libraries).
Quick links:
| [Getting Started](https://learn.microsoft.com/azure/active-directory/develop/web-app-quickstart?pivots=devlang-python)| [Docs](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki) | [Samples](https://aka.ms/aaddevsamplesv2) | [Support](README.md#community-help-and-support) | [Feedback](https://forms.office.com/r/TMjZkDbzjY) |
| --- | --- | --- | --- | --- |
## Scenarios supported
Click on the following thumbnail to visit a large map with clickable links to proper samples.
[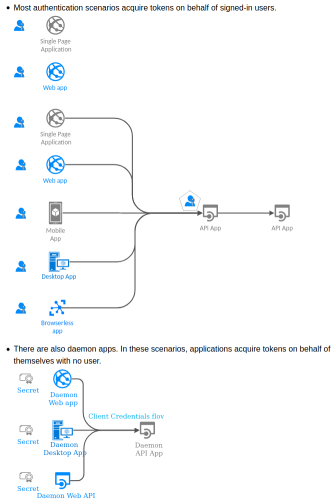](https://msal-python.readthedocs.io/en/latest/)
## Installation
You can find MSAL Python on [Pypi](https://pypi.org/project/msal/).
1. If you haven't already, [install and/or upgrade the pip](https://pip.pypa.io/en/stable/installing/)
of your Python environment to a recent version. We tested with pip 18.1.
1. As usual, just run `pip install msal`.
## Versions
This library follows [Semantic Versioning](http://semver.org/).
You can find the changes for each version under
[Releases](https://github.com/AzureAD/microsoft-authentication-library-for-python/releases).
## Usage
Before using MSAL Python (or any MSAL SDKs, for that matter), you will have to
[register your application with the Microsoft identity platform](https://docs.microsoft.com/azure/active-directory/develop/quickstart-v2-register-an-app).
Acquiring tokens with MSAL Python follows this 3-step pattern.
(Note: That is the high level conceptual pattern.
There will be some variations for different flows. They are demonstrated in
[runnable samples hosted right in this repo](https://github.com/AzureAD/microsoft-authentication-library-for-python/tree/dev/sample).
)
1. MSAL proposes a clean separation between
[public client applications, and confidential client applications](https://tools.ietf.org/html/rfc6749#section-2.1).
So you will first create either a `PublicClientApplication` or a `ConfidentialClientApplication` instance,
and ideally reuse it during the lifecycle of your app. The following example shows a `PublicClientApplication`:
```python
from msal import PublicClientApplication
app = PublicClientApplication(
"your_client_id",
authority="https://login.microsoftonline.com/Enter_the_Tenant_Name_Here")
```
Later, each time you would want an access token, you start by:
```python
result = None # It is just an initial value. Please follow instructions below.
```
2. The API model in MSAL provides you explicit control on how to utilize token cache.
This cache part is technically optional, but we highly recommend you to harness the power of MSAL cache.
It will automatically handle the token refresh for you.
```python
# We now check the cache to see
# whether we already have some accounts that the end user already used to sign in before.
accounts = app.get_accounts()
if accounts:
# If so, you could then somehow display these accounts and let end user choose
print("Pick the account you want to use to proceed:")
for a in accounts:
print(a["username"])
# Assuming the end user chose this one
chosen = accounts[0]
# Now let's try to find a token in cache for this account
result = app.acquire_token_silent(["your_scope"], account=chosen)
```
3. Either there is no suitable token in the cache, or you chose to skip the previous step,
now it is time to actually send a request to AAD to obtain a token.
There are different methods based on your client type and scenario. Here we demonstrate a placeholder flow.
```python
if not result:
# So no suitable token exists in cache. Let's get a new one from AAD.
result = app.acquire_token_by_one_of_the_actual_method(..., scopes=["User.Read"])
if "access_token" in result:
print(result["access_token"]) # Yay!
else:
print(result.get("error"))
print(result.get("error_description"))
print(result.get("correlation_id")) # You may need this when reporting a bug
```
Refer the [Wiki](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki) pages for more details on the MSAL Python functionality and usage.
## Migrating from ADAL
If your application is using ADAL Python, we recommend you to update to use MSAL Python. No new feature work will be done in ADAL Python.
See the [ADAL to MSAL migration](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Migrate-to-MSAL-Python) guide.
## Roadmap
You can follow the latest updates and plans for MSAL Python in the [Roadmap](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Roadmap) published on our Wiki.
## Samples and Documentation
MSAL Python supports multiple [application types and authentication scenarios](https://docs.microsoft.com/azure/active-directory/develop/authentication-flows-app-scenarios).
The generic documents on
[Auth Scenarios](https://docs.microsoft.com/azure/active-directory/develop/authentication-scenarios)
and
[Auth protocols](https://docs.microsoft.com/azure/active-directory/develop/active-directory-v2-protocols)
are recommended reading.
We provide a [full suite of sample applications](https://aka.ms/aaddevsamplesv2) and [documentation](https://aka.ms/aaddevv2) to help you get started with learning the Microsoft identity platform.
## Community Help and Support
We leverage Stack Overflow to work with the community on supporting Microsoft Entra and its SDKs, including this one!
We highly recommend you ask your questions on Stack Overflow (we're all on there!)
Also browser existing issues to see if someone has had your question before.
We recommend you use the "msal" tag so we can see it!
Here is the latest Q&A on Stack Overflow for MSAL:
[http://stackoverflow.com/questions/tagged/msal](http://stackoverflow.com/questions/tagged/msal)
## Submit Feedback
We'd like your thoughts on this library. Please complete [this short survey.](https://forms.office.com/r/TMjZkDbzjY)
## Security Reporting
If you find a security issue with our libraries or services please report it to [secure@microsoft.com](mailto:secure@microsoft.com) with as much detail as possible. Your submission may be eligible for a bounty through the [Microsoft Bounty](http://aka.ms/bugbounty) program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting [this page](https://technet.microsoft.com/security/dd252948) and subscribing to Security Advisory Alerts.
## Contributing
All code is licensed under the MIT license and we triage actively on GitHub. We enthusiastically welcome contributions and feedback. Please read the [contributing guide](./contributing.md) before starting.
## We Value and Adhere to the Microsoft Open Source Code of Conduct
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/). For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.
Raw data
{
"_id": null,
"home_page": "https://github.com/AzureAD/microsoft-authentication-library-for-python",
"name": "msal",
"maintainer": null,
"docs_url": null,
"requires_python": ">=3.7",
"maintainer_email": null,
"keywords": null,
"author": "Microsoft Corporation",
"author_email": "nugetaad@microsoft.com",
"download_url": "https://files.pythonhosted.org/packages/d5/da/81acbe0c1fd7e9e4ec35f55dadeba9833a847b9a6ba2e2d1e4432da901dd/msal-1.33.0.tar.gz",
"platform": null,
"description": "# Microsoft Authentication Library (MSAL) for Python\n\n| `dev` branch | Reference Docs | # of Downloads per different platforms | # of Downloads per recent MSAL versions | Benchmark Diagram |\n|:------------:|:--------------:|:--------------------------------------:|:---------------------------------------:|:-----------------:|\n [](https://github.com/AzureAD/microsoft-authentication-library-for-python/actions) | [](https://msal-python.readthedocs.io/en/latest/?badge=latest) | [](https://pypistats.org/packages/msal) | [](https://pepy.tech/project/msal) | [\ud83d\udcc9](https://azuread.github.io/microsoft-authentication-library-for-python/dev/bench/)\n\nThe Microsoft Authentication Library for Python enables applications to integrate with the [Microsoft identity platform](https://aka.ms/aaddevv2). It allows you to sign in users or apps with Microsoft identities ([Microsoft Entra ID](https://www.microsoft.com/security/business/identity-access/microsoft-entra-id), [External identities](https://www.microsoft.com/security/business/identity-access/microsoft-entra-external-id), [Microsoft Accounts](https://account.microsoft.com) and [Azure AD B2C](https://azure.microsoft.com/services/active-directory-b2c/) accounts) and obtain tokens to call Microsoft APIs such as [Microsoft Graph](https://graph.microsoft.io/) or your own APIs registered with the Microsoft identity platform. It is built using industry standard OAuth2 and OpenID Connect protocols\n\nNot sure whether this is the SDK you are looking for your app? There are other Microsoft Identity SDKs\n[here](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Microsoft-Authentication-Client-Libraries).\n\nQuick links:\n\n| [Getting Started](https://learn.microsoft.com/azure/active-directory/develop/web-app-quickstart?pivots=devlang-python)| [Docs](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki) | [Samples](https://aka.ms/aaddevsamplesv2) | [Support](README.md#community-help-and-support) | [Feedback](https://forms.office.com/r/TMjZkDbzjY) |\n| --- | --- | --- | --- | --- |\n\n## Scenarios supported\n\nClick on the following thumbnail to visit a large map with clickable links to proper samples.\n\n[](https://msal-python.readthedocs.io/en/latest/)\n\n## Installation\n\nYou can find MSAL Python on [Pypi](https://pypi.org/project/msal/).\n\n1. If you haven't already, [install and/or upgrade the pip](https://pip.pypa.io/en/stable/installing/)\n of your Python environment to a recent version. We tested with pip 18.1.\n1. As usual, just run `pip install msal`.\n\n## Versions\n\nThis library follows [Semantic Versioning](http://semver.org/).\n\nYou can find the changes for each version under\n[Releases](https://github.com/AzureAD/microsoft-authentication-library-for-python/releases).\n\n## Usage\n\nBefore using MSAL Python (or any MSAL SDKs, for that matter), you will have to\n[register your application with the Microsoft identity platform](https://docs.microsoft.com/azure/active-directory/develop/quickstart-v2-register-an-app).\n\nAcquiring tokens with MSAL Python follows this 3-step pattern.\n(Note: That is the high level conceptual pattern.\nThere will be some variations for different flows. They are demonstrated in\n[runnable samples hosted right in this repo](https://github.com/AzureAD/microsoft-authentication-library-for-python/tree/dev/sample).\n)\n\n\n1. MSAL proposes a clean separation between\n [public client applications, and confidential client applications](https://tools.ietf.org/html/rfc6749#section-2.1).\n So you will first create either a `PublicClientApplication` or a `ConfidentialClientApplication` instance,\n and ideally reuse it during the lifecycle of your app. The following example shows a `PublicClientApplication`:\n\n ```python\n from msal import PublicClientApplication\n app = PublicClientApplication(\n \"your_client_id\",\n authority=\"https://login.microsoftonline.com/Enter_the_Tenant_Name_Here\")\n ```\n\n Later, each time you would want an access token, you start by:\n ```python\n result = None # It is just an initial value. Please follow instructions below.\n ```\n\n2. The API model in MSAL provides you explicit control on how to utilize token cache.\n This cache part is technically optional, but we highly recommend you to harness the power of MSAL cache.\n It will automatically handle the token refresh for you.\n\n ```python\n # We now check the cache to see\n # whether we already have some accounts that the end user already used to sign in before.\n accounts = app.get_accounts()\n if accounts:\n # If so, you could then somehow display these accounts and let end user choose\n print(\"Pick the account you want to use to proceed:\")\n for a in accounts:\n print(a[\"username\"])\n # Assuming the end user chose this one\n chosen = accounts[0]\n # Now let's try to find a token in cache for this account\n result = app.acquire_token_silent([\"your_scope\"], account=chosen)\n ```\n\n3. Either there is no suitable token in the cache, or you chose to skip the previous step,\n now it is time to actually send a request to AAD to obtain a token.\n There are different methods based on your client type and scenario. Here we demonstrate a placeholder flow.\n\n ```python\n if not result:\n # So no suitable token exists in cache. Let's get a new one from AAD.\n result = app.acquire_token_by_one_of_the_actual_method(..., scopes=[\"User.Read\"])\n if \"access_token\" in result:\n print(result[\"access_token\"]) # Yay!\n else:\n print(result.get(\"error\"))\n print(result.get(\"error_description\"))\n print(result.get(\"correlation_id\")) # You may need this when reporting a bug\n ```\n\nRefer the [Wiki](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki) pages for more details on the MSAL Python functionality and usage.\n\n## Migrating from ADAL\n\nIf your application is using ADAL Python, we recommend you to update to use MSAL Python. No new feature work will be done in ADAL Python.\n\nSee the [ADAL to MSAL migration](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Migrate-to-MSAL-Python) guide.\n\n## Roadmap\n\nYou can follow the latest updates and plans for MSAL Python in the [Roadmap](https://github.com/AzureAD/microsoft-authentication-library-for-python/wiki/Roadmap) published on our Wiki.\n\n## Samples and Documentation\n\nMSAL Python supports multiple [application types and authentication scenarios](https://docs.microsoft.com/azure/active-directory/develop/authentication-flows-app-scenarios).\nThe generic documents on\n[Auth Scenarios](https://docs.microsoft.com/azure/active-directory/develop/authentication-scenarios)\nand\n[Auth protocols](https://docs.microsoft.com/azure/active-directory/develop/active-directory-v2-protocols)\nare recommended reading.\n\nWe provide a [full suite of sample applications](https://aka.ms/aaddevsamplesv2) and [documentation](https://aka.ms/aaddevv2) to help you get started with learning the Microsoft identity platform.\n\n## Community Help and Support\n\nWe leverage Stack Overflow to work with the community on supporting Microsoft Entra and its SDKs, including this one!\nWe highly recommend you ask your questions on Stack Overflow (we're all on there!)\nAlso browser existing issues to see if someone has had your question before.\n\nWe recommend you use the \"msal\" tag so we can see it!\nHere is the latest Q&A on Stack Overflow for MSAL:\n[http://stackoverflow.com/questions/tagged/msal](http://stackoverflow.com/questions/tagged/msal)\n\n## Submit Feedback\n\nWe'd like your thoughts on this library. Please complete [this short survey.](https://forms.office.com/r/TMjZkDbzjY)\n\n## Security Reporting\n\nIf you find a security issue with our libraries or services please report it to [secure@microsoft.com](mailto:secure@microsoft.com) with as much detail as possible. Your submission may be eligible for a bounty through the [Microsoft Bounty](http://aka.ms/bugbounty) program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting [this page](https://technet.microsoft.com/security/dd252948) and subscribing to Security Advisory Alerts.\n\n## Contributing\n\nAll code is licensed under the MIT license and we triage actively on GitHub. We enthusiastically welcome contributions and feedback. Please read the [contributing guide](./contributing.md) before starting.\n\n## We Value and Adhere to the Microsoft Open Source Code of Conduct\n\nThis project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/). For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [opencode@microsoft.com](mailto:opencode@microsoft.com) with any additional questions or comments.\n",
"bugtrack_url": null,
"license": "MIT",
"summary": "The Microsoft Authentication Library (MSAL) for Python library enables your app to access the Microsoft Cloud by supporting authentication of users with Microsoft Azure Active Directory accounts (AAD) and Microsoft Accounts (MSA) using industry standard OAuth2 and OpenID Connect.",
"version": "1.33.0",
"project_urls": {
"Changelog": "https://github.com/AzureAD/microsoft-authentication-library-for-python/releases",
"Documentation": "https://msal-python.readthedocs.io/",
"Feature/Bug Tracker": "https://github.com/AzureAD/microsoft-authentication-library-for-python/issues",
"Homepage": "https://github.com/AzureAD/microsoft-authentication-library-for-python",
"Questions": "https://stackoverflow.com/questions/tagged/azure-ad-msal+python"
},
"split_keywords": [],
"urls": [
{
"comment_text": null,
"digests": {
"blake2b_256": "865bfbc73e91f7727ae1e79b21ed833308e99dc11cc1cd3d4717f579775de5e9",
"md5": "9eec00e0cb2d3707ef2a2b4a1bce964e",
"sha256": "c0cd41cecf8eaed733ee7e3be9e040291eba53b0f262d3ae9c58f38b04244273"
},
"downloads": -1,
"filename": "msal-1.33.0-py3-none-any.whl",
"has_sig": false,
"md5_digest": "9eec00e0cb2d3707ef2a2b4a1bce964e",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": ">=3.7",
"size": 116853,
"upload_time": "2025-07-22T19:36:32",
"upload_time_iso_8601": "2025-07-22T19:36:32.403606Z",
"url": "https://files.pythonhosted.org/packages/86/5b/fbc73e91f7727ae1e79b21ed833308e99dc11cc1cd3d4717f579775de5e9/msal-1.33.0-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": null,
"digests": {
"blake2b_256": "d5da81acbe0c1fd7e9e4ec35f55dadeba9833a847b9a6ba2e2d1e4432da901dd",
"md5": "b0cf88719d00c011912cf181a6bfa7c0",
"sha256": "836ad80faa3e25a7d71015c990ce61f704a87328b1e73bcbb0623a18cbf17510"
},
"downloads": -1,
"filename": "msal-1.33.0.tar.gz",
"has_sig": false,
"md5_digest": "b0cf88719d00c011912cf181a6bfa7c0",
"packagetype": "sdist",
"python_version": "source",
"requires_python": ">=3.7",
"size": 153801,
"upload_time": "2025-07-22T19:36:33",
"upload_time_iso_8601": "2025-07-22T19:36:33.693353Z",
"url": "https://files.pythonhosted.org/packages/d5/da/81acbe0c1fd7e9e4ec35f55dadeba9833a847b9a6ba2e2d1e4432da901dd/msal-1.33.0.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2025-07-22 19:36:33",
"github": true,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"github_user": "AzureAD",
"github_project": "microsoft-authentication-library-for-python",
"travis_ci": false,
"coveralls": false,
"github_actions": true,
"requirements": [],
"tox": true,
"lcname": "msal"
}
