<!--
SPDX-FileCopyrightText: 2023 Jeff Epler
SPDX-License-Identifier: MIT
-->
# textual-totp: TOTP (authenticator) application using Python & Textual
# Installation
You can install textual-totp with pip or pipx:
```
pipx install textual-totp
```
# Configuration
Configuration is in the form of a TOML file inside the user's standard configuration
directory. On Linux, this is `~/.config/ttotp/settings.toml`.
At startup, `ttotp` invokes a program that prints out TOTP URIs, one per line.
The author recommends storing your TOTPs in
[pass, the standard unix password manager](https://www.passwordstore.org/).
In this case, you would configure with a command like
```toml
otp-command = ['pass', 'show', 'totp-tokens']
```
If you hate security, you can use an insecure command like `cat`, or just test things with `echo`:
```toml
otp-command = "echo 'otpauth://totp/example?algorithm=SHA1&digits=6&secret=IHACDTJ2TFCSLUJLMSHYDBD74FS7OY5B'"
```
If the command is a string, it is interpreted with the shell; otherwise, the list of arguments is used directly.
## Auto-exit on idle
To auto exit after a specified inactivity period, use the `auto-exit` setting:
```toml
# Exit after 5 minutes (300 seconds) of inactivity
auto-exit = 300
```
Any key event, mouse click, or mouse scroll counts as "activity" and will reset the auto exit timer.
If `auto-exit` is not specified, or it is 0, there is no inactivity timeout.
## Profiles
textual-totp supports multiple profiles. Profiles are organized as sections of the configuration file; if a setting is not specified within a profile section, the global setting is used.
For example, given
```
auto-exit=300
otp-command = ["..."]
[trusted-location]
auto-exit=0
```
textual-totp will normally exit after 5 minutes of inactivity, but when you run `ttotp --profile trusted-location` auto-exit will be disabled.
# Obtaining TOTP URIs
There are a couple of ways to obtain your TOTP URIs, which are strings that begin `otpauth://totp/`.
* Scan individual QR codes when signing up for 2FA
* You can photograph or screen capture and then locally decode QR codes using a compatible tool such as [PyQRCode](https://pypi.org/project/PyQRCode/)
* Scan the QR code(s) from Google Authenticator's "transfer accounts" feature. These are in the form of an "offline otpauth-migration" URL. Decode these with a compatible tool, such as [otpauth-migration-decode](https://github.com/trewlgns/otpauth-migration-decode)
* Android does not permit this from being screenshotted, but your laptop probably has a camera
* Transcribe the lengthy alphanumeric code that is shown during some 2FA signup processes into a complete otpauth URL, removing any whitespace that is present.
There are browser-based tools for helping with some of these tasks.
However, it is difficult to determine whether web pages treat data safely.
Therefore, none are recommended in this section.
# Using textual-totp
The command to start textual-totp is `ttotp`.
It has several options which can be shown with `ttotp --help`.
`ttotp` will first invoke the `otp-command` to get the list of TOTPs.
This may require interaction
(for instance, the `pass` command may need to request your GPG key passphrase)
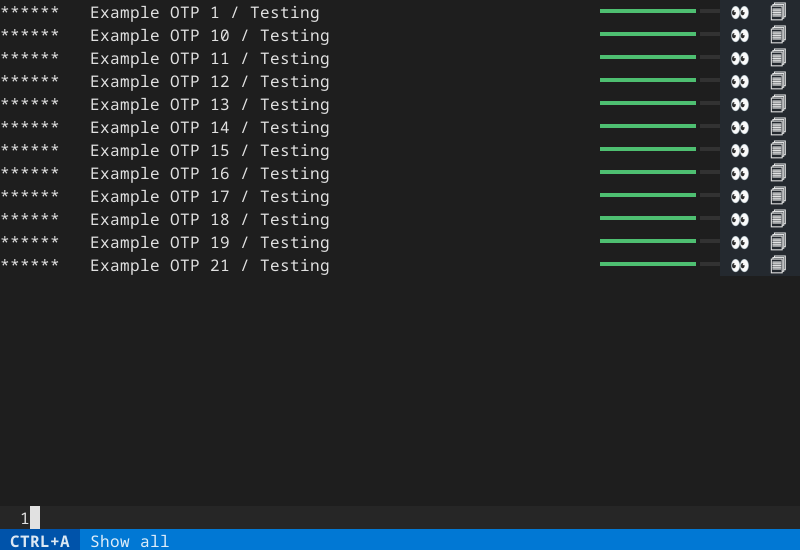
Once the otp-command finishes, `ttotp` will show each available TOTP.
Each code will show as `******` until it is revealed.
Navigate up/down in several ways:
* up and down keys
* tab and shift-tab keys
* "j" and "k" (vi keys)
To reveal a code, move to the desired line and press "s".
When the code expires, it will be replaced with `******` again.
Copy a code directly to the operating system's clipboard by pressing "c".
The code will be cleared from the clipboard after 30 seconds.
Your Operating System may report that `ttotp` "pasted from the clipboard".
This is because `ttotp` tries to only clear values that it set,
by checking that the current clipboard value is equal to the value it pasted earlier.
Search for a key by pressing "/" and then entering sub-strings to search for.
Press Ctrl+A to show all keys again.
Textual's built in [fuzzy match](https://textual.textualize.io/api/fuzzy_matcher/) algorithm is used.
This makes it easy to search for e.g., "Jay Doe / example.com" by entering "ja d ex", while not requiring any sophisticated fuzzy search technology.
Due to the simple way this is implemented, a space character inside a character class does not function as expected.
Since complicated regular expressions are likely seldom used, this is not likely to be a huge limitation.
Exit the app with Ctrl+C.
# In-memory storage of TOTPs
As long as `ttotp` is open, the TOTP secret values are stored in memory in plain text.
`ttotp` never writes secret values to operating system files or stores them in environment variables.
(but your otp-command might! check any related documentation carefully)
# Development Status
I (@jepler) wrote this software because it was useful to me. It fits my needs
in its current form. I maintain it for my own needs and acting on issues and
pull requests is unlikely to be a high priority. Thank you for your understanding about this!
I develop the software on Linux, generally Debian Linux. I often make
compatibility with Debian Oldstable my goal, but this package has only been
tested on stable Debian Bookworm with Python 3.11 and almost certainly uses
constructs not in Python 3.9. Improvements for compatibility on other platforms
are welcome.
In the unlikely event that this project becomes popular, I would want to
convert it to a community-run project with multiple maintainers. There are some
issues in the tracker entered by me that seem like good directions to develop
the software in.
Raw data
{
"_id": null,
"home_page": null,
"name": "textual-totp",
"maintainer": null,
"docs_url": null,
"requires_python": ">=3.11",
"maintainer_email": null,
"keywords": "otp, totp, 2fa, authenticator",
"author": null,
"author_email": "Jeff Epler <jepler@gmail.com>",
"download_url": "https://files.pythonhosted.org/packages/8f/70/c56b751247527878698b4c7d3b2d3b2971f9e6e29fe3316ec027dab5ac64/textual_totp-0.9.5.tar.gz",
"platform": null,
"description": "<!--\nSPDX-FileCopyrightText: 2023 Jeff Epler\n\nSPDX-License-Identifier: MIT\n-->\n\n# textual-totp: TOTP (authenticator) application using Python & Textual\n\n\n\n# Installation\n\nYou can install textual-totp with pip or pipx:\n```\npipx install textual-totp\n```\n\n# Configuration\n\nConfiguration is in the form of a TOML file inside the user's standard configuration\ndirectory. On Linux, this is `~/.config/ttotp/settings.toml`.\n\nAt startup, `ttotp` invokes a program that prints out TOTP URIs, one per line.\nThe author recommends storing your TOTPs in\n[pass, the standard unix password manager](https://www.passwordstore.org/).\nIn this case, you would configure with a command like\n```toml\notp-command = ['pass', 'show', 'totp-tokens']\n```\n\nIf you hate security, you can use an insecure command like `cat`, or just test things with `echo`:\n```toml\notp-command = \"echo 'otpauth://totp/example?algorithm=SHA1&digits=6&secret=IHACDTJ2TFCSLUJLMSHYDBD74FS7OY5B'\"\n```\n\nIf the command is a string, it is interpreted with the shell; otherwise, the list of arguments is used directly.\n\n## Auto-exit on idle\n\nTo auto exit after a specified inactivity period, use the `auto-exit` setting:\n```toml\n# Exit after 5 minutes (300 seconds) of inactivity\nauto-exit = 300\n```\nAny key event, mouse click, or mouse scroll counts as \"activity\" and will reset the auto exit timer.\n\nIf `auto-exit` is not specified, or it is 0, there is no inactivity timeout.\n\n## Profiles\n\ntextual-totp supports multiple profiles. Profiles are organized as sections of the configuration file; if a setting is not specified within a profile section, the global setting is used.\n\nFor example, given\n```\nauto-exit=300\notp-command = [\"...\"]\n[trusted-location]\nauto-exit=0\n```\ntextual-totp will normally exit after 5 minutes of inactivity, but when you run `ttotp --profile trusted-location` auto-exit will be disabled.\n\n# Obtaining TOTP URIs\n\nThere are a couple of ways to obtain your TOTP URIs, which are strings that begin `otpauth://totp/`.\n\n * Scan individual QR codes when signing up for 2FA\n * You can photograph or screen capture and then locally decode QR codes using a compatible tool such as [PyQRCode](https://pypi.org/project/PyQRCode/)\n * Scan the QR code(s) from Google Authenticator's \"transfer accounts\" feature. These are in the form of an \"offline otpauth-migration\" URL. Decode these with a compatible tool, such as [otpauth-migration-decode](https://github.com/trewlgns/otpauth-migration-decode)\n * Android does not permit this from being screenshotted, but your laptop probably has a camera\n * Transcribe the lengthy alphanumeric code that is shown during some 2FA signup processes into a complete otpauth URL, removing any whitespace that is present.\n\nThere are browser-based tools for helping with some of these tasks.\nHowever, it is difficult to determine whether web pages treat data safely.\nTherefore, none are recommended in this section.\n\n# Using textual-totp\n\nThe command to start textual-totp is `ttotp`.\nIt has several options which can be shown with `ttotp --help`.\n\n`ttotp` will first invoke the `otp-command` to get the list of TOTPs.\nThis may require interaction\n(for instance, the `pass` command may need to request your GPG key passphrase)\n\nOnce the otp-command finishes, `ttotp` will show each available TOTP.\nEach code will show as `******` until it is revealed.\n\nNavigate up/down in several ways:\n * up and down keys\n * tab and shift-tab keys\n * \"j\" and \"k\" (vi keys)\n\nTo reveal a code, move to the desired line and press \"s\".\nWhen the code expires, it will be replaced with `******` again.\n\nCopy a code directly to the operating system's clipboard by pressing \"c\".\nThe code will be cleared from the clipboard after 30 seconds.\nYour Operating System may report that `ttotp` \"pasted from the clipboard\".\nThis is because `ttotp` tries to only clear values that it set,\nby checking that the current clipboard value is equal to the value it pasted earlier.\n\nSearch for a key by pressing \"/\" and then entering sub-strings to search for.\nPress Ctrl+A to show all keys again.\n\nTextual's built in [fuzzy match](https://textual.textualize.io/api/fuzzy_matcher/) algorithm is used.\n\nThis makes it easy to search for e.g., \"Jay Doe / example.com\" by entering \"ja d ex\", while not requiring any sophisticated fuzzy search technology.\n\nDue to the simple way this is implemented, a space character inside a character class does not function as expected.\nSince complicated regular expressions are likely seldom used, this is not likely to be a huge limitation.\n\nExit the app with Ctrl+C.\n\n# In-memory storage of TOTPs\nAs long as `ttotp` is open, the TOTP secret values are stored in memory in plain text.\n\n`ttotp` never writes secret values to operating system files or stores them in environment variables.\n(but your otp-command might! check any related documentation carefully)\n\n# Development Status\n\nI (@jepler) wrote this software because it was useful to me. It fits my needs\nin its current form. I maintain it for my own needs and acting on issues and\npull requests is unlikely to be a high priority. Thank you for your understanding about this!\n\nI develop the software on Linux, generally Debian Linux. I often make\ncompatibility with Debian Oldstable my goal, but this package has only been\ntested on stable Debian Bookworm with Python 3.11 and almost certainly uses\nconstructs not in Python 3.9. Improvements for compatibility on other platforms\nare welcome.\n\nIn the unlikely event that this project becomes popular, I would want to\nconvert it to a community-run project with multiple maintainers. There are some\nissues in the tracker entered by me that seem like good directions to develop\nthe software in.\n",
"bugtrack_url": null,
"license": null,
"summary": "TOTP (authenticator) application using Python & Textual",
"version": "0.9.5",
"project_urls": {
"homepage": "https://github.com/jepler/textual-totp",
"repository": "https://github.com/jepler/textual-totp"
},
"split_keywords": [
"otp",
" totp",
" 2fa",
" authenticator"
],
"urls": [
{
"comment_text": null,
"digests": {
"blake2b_256": "9119601b346476b0cf13e6fe34a048375eae16aebc051f6fb7c85fb2d1e420b5",
"md5": "2aba8e6dd0ee19edcf143a0089803e0e",
"sha256": "b0a300d5c708498acc5860548734c901da86272e9c3dcfad381fef3488332de1"
},
"downloads": -1,
"filename": "textual_totp-0.9.5-py3-none-any.whl",
"has_sig": false,
"md5_digest": "2aba8e6dd0ee19edcf143a0089803e0e",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": ">=3.11",
"size": 11402,
"upload_time": "2025-08-17T17:21:08",
"upload_time_iso_8601": "2025-08-17T17:21:08.713988Z",
"url": "https://files.pythonhosted.org/packages/91/19/601b346476b0cf13e6fe34a048375eae16aebc051f6fb7c85fb2d1e420b5/textual_totp-0.9.5-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": null,
"digests": {
"blake2b_256": "8f70c56b751247527878698b4c7d3b2d3b2971f9e6e29fe3316ec027dab5ac64",
"md5": "19713ea02bfba187808bba1043bf187a",
"sha256": "d6e3421969a6de27cfa68ea72d5ed88a652f55ba37895d74bae20c43fa12c807"
},
"downloads": -1,
"filename": "textual_totp-0.9.5.tar.gz",
"has_sig": false,
"md5_digest": "19713ea02bfba187808bba1043bf187a",
"packagetype": "sdist",
"python_version": "source",
"requires_python": ">=3.11",
"size": 49831,
"upload_time": "2025-08-17T17:21:10",
"upload_time_iso_8601": "2025-08-17T17:21:10.195758Z",
"url": "https://files.pythonhosted.org/packages/8f/70/c56b751247527878698b4c7d3b2d3b2971f9e6e29fe3316ec027dab5ac64/textual_totp-0.9.5.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2025-08-17 17:21:10",
"github": true,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"github_user": "jepler",
"github_project": "textual-totp",
"travis_ci": false,
"coveralls": false,
"github_actions": true,
"requirements": [
{
"name": "click",
"specs": []
},
{
"name": "platformdirs",
"specs": []
},
{
"name": "pyotp",
"specs": []
},
{
"name": "pyperclip",
"specs": []
},
{
"name": "textual",
"specs": [
[
">=",
"3.1.0"
]
]
}
],
"lcname": "textual-totp"
}
