# CVE Prioritizer
CVE Prioritizer is a powerful tool that helps you prioritize vulnerability patching by combining
[CVSS](https://nvd.nist.gov/vuln-metrics/cvss#), [EPSS](https://www.first.org/epss/data_stats),
CISA's [Known Exploited Vulnerabilities](https://www.cisa.gov/known-exploited-vulnerabilities-catalog) and VulnCheck's community resources (
[NVD++](https://docs.vulncheck.com/community/nist-nvd/introduction),
[KEV](https://docs.vulncheck.com/community/vulncheck-kev/introduction)).
It provides valuable insights into the likelihood of exploitation and the
potential impact of vulnerabilities on your information system.
## Why Combine CVSS, EPSS, and CISA KEV?
CVE_Prioritizer leverages the correlation between CVSS and EPSS scores to enhance vulnerability remediation efforts.
While CVSS captures the fundamental properties of a vulnerability, EPSS offers data-driven threat information,
enabling you to better prioritize patching.
## Table of Contents
1. [Why Combine CVSS, EPSS and KEV?](#why-combine-cvss,-epss,and-cisa-kev?)
2. [Combining CVSS, EPSS and KEV](#combining-cvss,-epss,and-kev)
3. [Our Approach](#our-approach)
4. [Installation](#installation)
5. [Usage](#usage)
- Request API Keys
- Select Your CVE Data Source
- Choose Input Method
- Tailor the Output
6. [Examples](#examples)
7. [Contributing](#contributing)
8. [License](#license)
9. [Contact](#contact)
## Combining CVSS, EPSS and KEV
The team at FIRST did an amazing job explaining why one would want to combine CVSS and EPSS in their
[EPSS User Guide](https://www.first.org/epss/user-guide). The following material has been extracted from that document.
The figure below shows the correlation between EPSS and CVSS scores based on data from 05-16-2021. Recall that EPSS
produces prediction scores between 0 and 1 (0 and 100%) where higher scores suggest higher probability of exploit.
Each dot represents one or more vulnerabilities (CVEs). Some vulnerabilities are labeled for illustrative purposes.
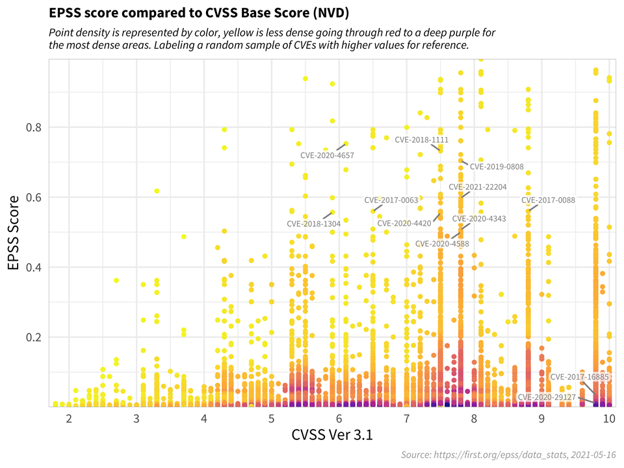
First, observe how most vulnerabilities are concentrated near the bottom of the plot, and only a small percent of
vulnerabilities have EPSS scores above 50% (0.5). While there is some correlation between EPSS and CVSS scores, overall,
this plot provides suggestive evidence that attackers are not only targeting vulnerabilities that produce the greatest
impact, or are necessarily easier to exploit (such as for example, an unauthenticated remote code execution).
This is an important finding because it refutes a common assumption that attackers are only looking for (and using)
the most severe vulnerabilities. And so, how then can a network defender choose among these vulnerabilities when
deciding what to patch first?
CVSS is a useful tool for capturing the fundamental properties of a vulnerability, but it needs to be used in
combination with data-driven threat information, like EPSS, in order to better prioritize vulnerability remediation
efforts.
For the sake of discussion, consider the diagram below, which has been annotated to generally illustrate vulnerability
prioritization.
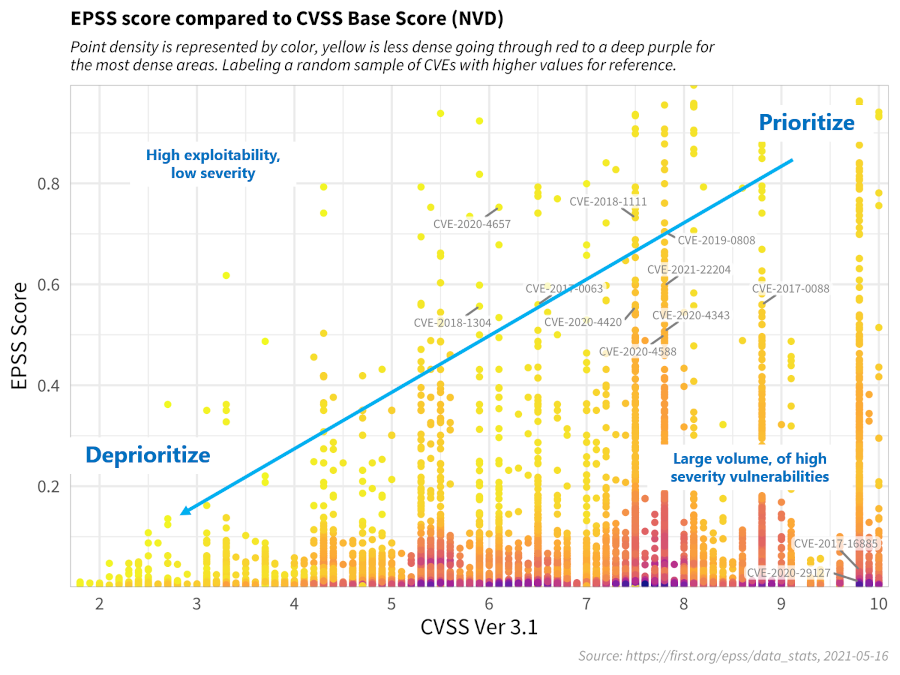
- Vulnerabilities in the **bottom left** represent those that have both a lower probability of being exploited, and would
incur a lower severity impact to the information system, and can therefore be **de-prioritized**.
- Vulnerabilities in the **upper left** quadrant may be more likely to be exploited, but, on their own, would not critically impact the
information system. (Further research, however, should be conducted in order to better understand how these sorts of
vulnerabilities may be used in a chained attack.)
- Vulnerabilities in the **bottom right** represent those that, while may severely impact the information system, are much
less likely to be exploited, relative to others, but should still be watched in the event that the threat landscape
changes.
- Vulnerabilities in the **upper right** quadrant, on the other hand, are the most critical kinds of vulnerabilities which
are both more likely to be exploited, and could fully compromise the information system, and should therefore be
patched first.
This decision strategy as described above emphasizes the tremendous capability of EPSS. A network defender who has
typically had to address thousands or tens of thousands of exposed vulnerabilities, is now able to spend fewer resources,
to patch more vulnerabilities that are much more likely to be exploited. This capability to differentiate among
vulnerabilities has never before been possible.
## Our Approach
We have refined the prioritization thresholds based on FIRST's recommendations and our own experience. Here's an overview:
1. We **include CISA's Known Exploited Vulnerabilities**, giving priority to CVEs found in KEV.
2. The **CVSS Threshold is set to 6.0**, representing the weighted average CVSS Score from [CVE Details](https://www.cvedetails.com/cvss-score-distribution.php).
3. The **EPSS Threshold is set to 0.2**, focusing on vulnerabilities with higher relevance above this threshold.
This approach categorizes vulnerabilities into five priority levels, allowing you to allocate resources more effectively.
| **Priority** | **Description** |
|--------------|----------------------------------|
| Priority 1+ | CVEs found in CISA's KEV |
| Priority 1 | CVEs in the Upper Right Quadrant |
| Priority 2 | CVEs in the Lower Right Quadrant |
| Priority 3 | CVEs in the Upper Left Quadrant |
| Priority 4 | CVEs in the Lower Left Quadrant |
Below is a modified version of FIRST's recommendation after applying our own approach.
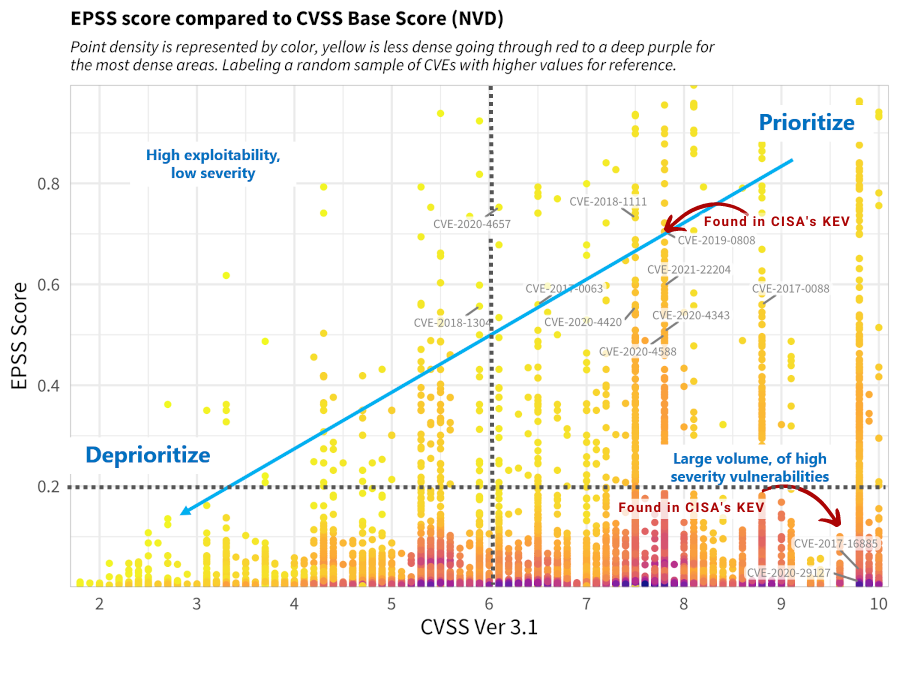
**Note:** You can define your own thresholds when running the tool to tailor the results
to your organization's risk appetite.
## Installation
### Github
```shell
git clone https://github.com/TURROKS/CVE_Prioritizer.git
cd CVE_Prioritizer
pip install -r requirements.txt
```
### pip
```shell
pip install --user cve_prioritizer
```
## Usage
To use CVE_Prioritizer effectively, follow these steps:
1. Request your API keys to avoid public rate limits:
- **NIST NVD:** Request [here](https://nvd.nist.gov/developers/request-an-api-key)
- **VULNCHECK (Fast):** Register [here](https://vulncheck.com/register).
- **Save APIs:** Use the `-sa` or `--set-api` option to save your API Keys in your `.env` file.
2. Select your CVE Data source:
- **NIST NVD:** Default.
- **[NVD++](https://vulncheck.com/nvd2):** Use `-vc` or `--vulncheck`.
- **VulnCheck KEV:** Use `-vck` or `vulnchek_kev` **(ONLY WORKS WITH NVD++)**.
3. Choose Input Method:
- **Single CVE:** Use the `-c` followed by the CVE ID.
- **List of CVEs:** Use `-l` followed by a **comma-separated** list of CVEs.
- **File with CVEs:** Use `-f` to import a file containing CVE IDs (one per line).
4. Tailor the output according to your needs:
- Use the `-v` or `--verbose` for detailed information.
- Define custom thresholds with `--cvss` and/or `--epss` to align the results with your organization's
risk appetite.
- Define the number of concurrent threads with `-t` or `--threads` (default: 100).
### Examples
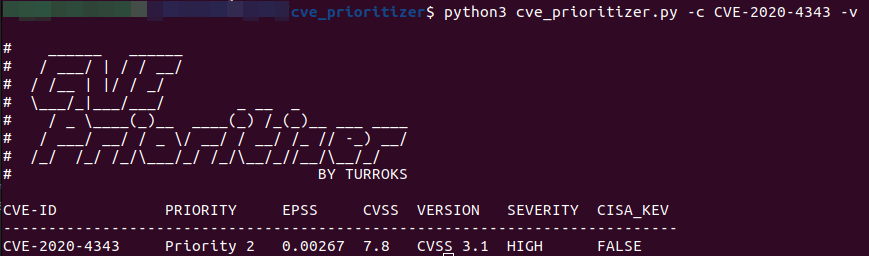
#### Single CVE
```
python3 cve_prioritizer.py -c CVE-2020-29127
```
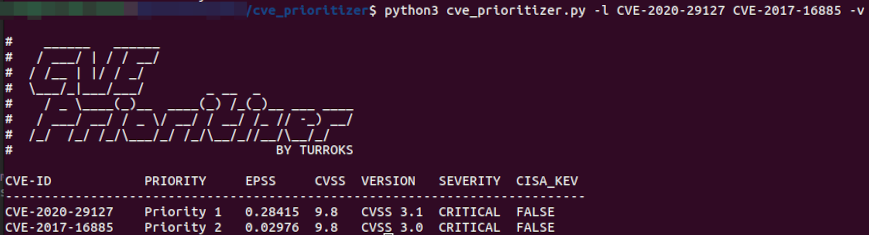
#### List of CVEs
```
python3 cve_prioritizer.py -l CVE-2020-29127,CVE-2017-16885
```
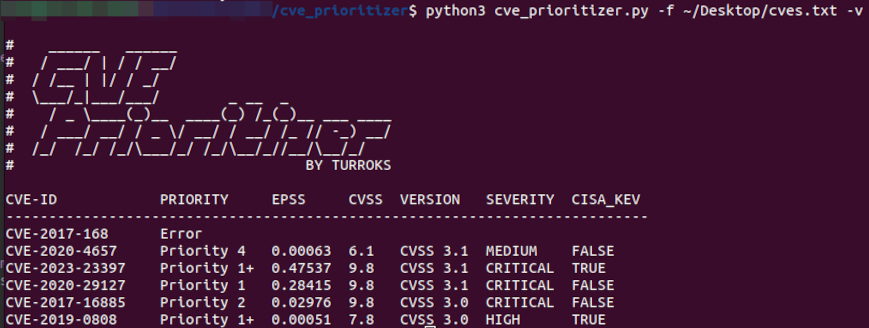
#### File with CVEs
You can also provide a text file with a list of CVEs (one per line)
```
python3 cve_prioritizer.py -f ~\Desktop\CheckTheseCVEs.txt
```
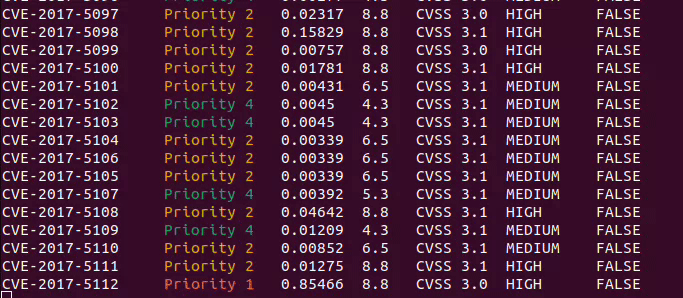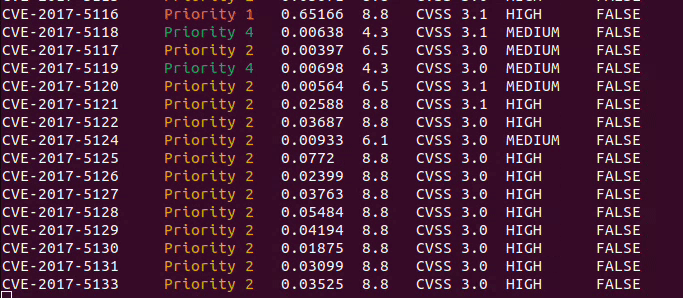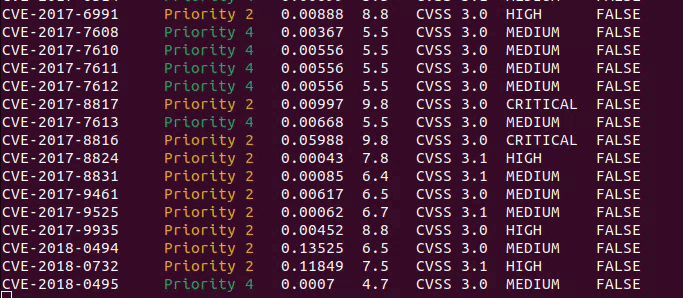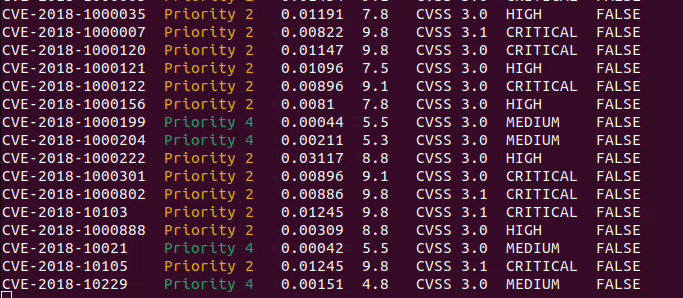
### Outputs
CVE_Prioritizer provides flexible output options to suit your preferences. By default, it provides a summary of results,
including the CVE-ID and its priority. However, you can enable verbose mode to obtain additional information.
Here are the available output options:
**Summary Results (default):** Provides a concise summary, including the CVE-ID and its priority.

**Verbose Mode:** Enables detailed output with the following information for each CVE:
- CVE ID
- Priority
- EPSS Score
- CVSS Base Score
- CVSS Version
- CVSS Severity
- KEV Status (TRUE or FALSE)
- Vendor
- Product
- CVSS Vector
**CSV File**
You can save the results to a CSV file by using the `-o` or `--output` flags
```
python3 cve_prioritizer.py -f cve_list.txt -o ~/Desktop/prioritized.csv
```
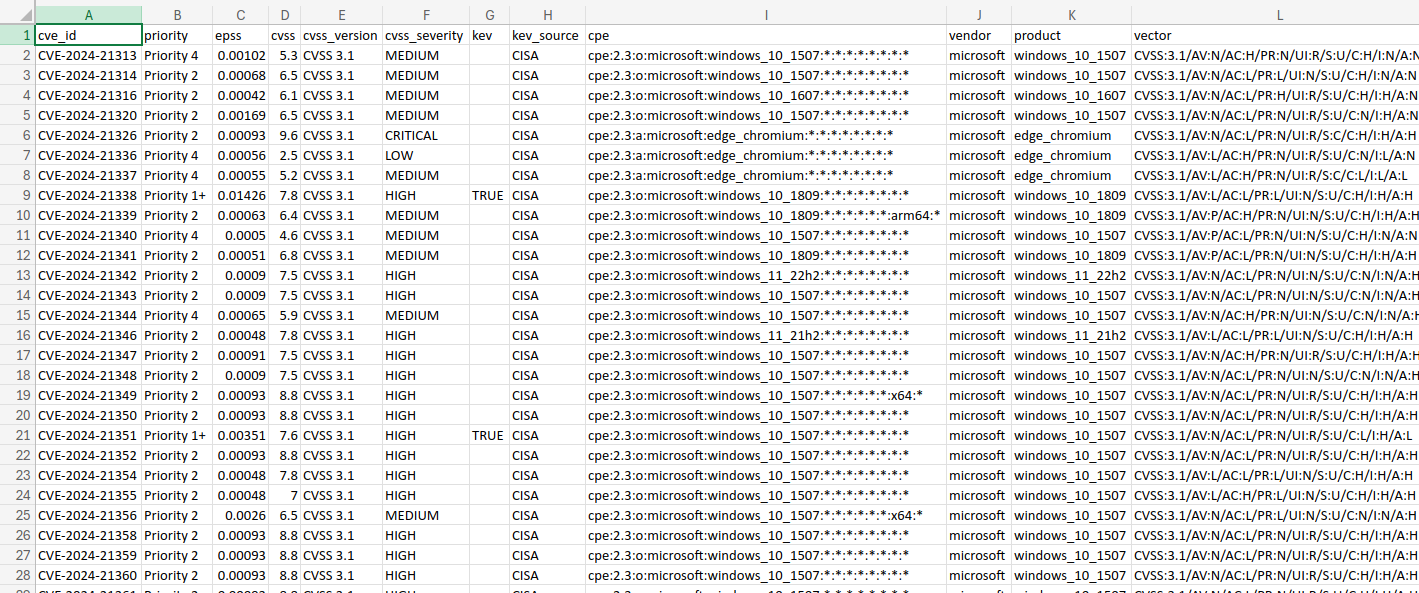
This outputs the verbose results independently of the terminal output that you use.
#### Contributing
Please refer to [CONTRIBUTING.md](https://raw.githubusercontent.com/TURROKS/CVE_Prioritizer/main/docs/CONTRIBUTING.md) for guidelines
#### License
This project is licensed under the BSD 3-Clause license - see the [LICENSE](https://raw.githubusercontent.com/TURROKS/CVE_Prioritizer/main/LICENSE) file for details.
#### Contact
For questions or issues, please contact me at prioritizer@proton.me
Happy Patching!
[](https://ko-fi.com/K3K4KOFV4)
#### NVD API Notice:
Please note that while this tool uses the NVD API, it is not endorsed or certified by the NVD.
Raw data
{
"_id": null,
"home_page": "https://github.com/TURROKS/CVE_Prioritizer",
"name": "CVE-Prioritizer",
"maintainer": null,
"docs_url": null,
"requires_python": ">=3.6",
"maintainer_email": null,
"keywords": null,
"author": "Mario Rojas",
"author_email": "prioritizer@proton.me",
"download_url": "https://files.pythonhosted.org/packages/38/2d/59901352efe96403995802cc8975c239ebc329d5cd2f755632bd4a768541/CVE_Prioritizer-1.7.2.tar.gz",
"platform": null,
"description": "# CVE Prioritizer\n\nCVE Prioritizer is a powerful tool that helps you prioritize vulnerability patching by combining\n[CVSS](https://nvd.nist.gov/vuln-metrics/cvss#), [EPSS](https://www.first.org/epss/data_stats),\nCISA's [Known Exploited Vulnerabilities](https://www.cisa.gov/known-exploited-vulnerabilities-catalog) and VulnCheck's community resources (\n[NVD++](https://docs.vulncheck.com/community/nist-nvd/introduction),\n[KEV](https://docs.vulncheck.com/community/vulncheck-kev/introduction)).\nIt provides valuable insights into the likelihood of exploitation and the\npotential impact of vulnerabilities on your information system.\n\n\n\n## Why Combine CVSS, EPSS, and CISA KEV?\n\nCVE_Prioritizer leverages the correlation between CVSS and EPSS scores to enhance vulnerability remediation efforts.\nWhile CVSS captures the fundamental properties of a vulnerability, EPSS offers data-driven threat information,\nenabling you to better prioritize patching.\n\n## Table of Contents\n\n1. [Why Combine CVSS, EPSS and KEV?](#why-combine-cvss,-epss,and-cisa-kev?)\n2. [Combining CVSS, EPSS and KEV](#combining-cvss,-epss,and-kev)\n3. [Our Approach](#our-approach)\n4. [Installation](#installation)\n5. [Usage](#usage)\n - Request API Keys\n - Select Your CVE Data Source\n - Choose Input Method\n - Tailor the Output\n6. [Examples](#examples)\n7. [Contributing](#contributing)\n8. [License](#license)\n9. [Contact](#contact)\n\n## Combining CVSS, EPSS and KEV\n\nThe team at FIRST did an amazing job explaining why one would want to combine CVSS and EPSS in their \n[EPSS User Guide](https://www.first.org/epss/user-guide). The following material has been extracted from that document. \n\nThe figure below shows the correlation between EPSS and CVSS scores based on data from 05-16-2021. Recall that EPSS \nproduces prediction scores between 0 and 1 (0 and 100%) where higher scores suggest higher probability of exploit. \nEach dot represents one or more vulnerabilities (CVEs). Some vulnerabilities are labeled for illustrative purposes.\n\n\n\nFirst, observe how most vulnerabilities are concentrated near the bottom of the plot, and only a small percent of \nvulnerabilities have EPSS scores above 50% (0.5). While there is some correlation between EPSS and CVSS scores, overall,\nthis plot provides suggestive evidence that attackers are not only targeting vulnerabilities that produce the greatest \nimpact, or are necessarily easier to exploit (such as for example, an unauthenticated remote code execution).\n\nThis is an important finding because it refutes a common assumption that attackers are only looking for (and using) \nthe most severe vulnerabilities. And so, how then can a network defender choose among these vulnerabilities when \ndeciding what to patch first?\n\nCVSS is a useful tool for capturing the fundamental properties of a vulnerability, but it needs to be used in \ncombination with data-driven threat information, like EPSS, in order to better prioritize vulnerability remediation \nefforts.\n\nFor the sake of discussion, consider the diagram below, which has been annotated to generally illustrate vulnerability \nprioritization.\n\n\n\n- Vulnerabilities in the **bottom left** represent those that have both a lower probability of being exploited, and would \nincur a lower severity impact to the information system, and can therefore be **de-prioritized**. \n- Vulnerabilities in the **upper left** quadrant may be more likely to be exploited, but, on their own, would not critically impact the \ninformation system. (Further research, however, should be conducted in order to better understand how these sorts of \nvulnerabilities may be used in a chained attack.)\n- Vulnerabilities in the **bottom right** represent those that, while may severely impact the information system, are much \nless likely to be exploited, relative to others, but should still be watched in the event that the threat landscape \nchanges.\n- Vulnerabilities in the **upper right** quadrant, on the other hand, are the most critical kinds of vulnerabilities which \nare both more likely to be exploited, and could fully compromise the information system, and should therefore be \npatched first.\n\nThis decision strategy as described above emphasizes the tremendous capability of EPSS. A network defender who has \ntypically had to address thousands or tens of thousands of exposed vulnerabilities, is now able to spend fewer resources, \nto patch more vulnerabilities that are much more likely to be exploited. This capability to differentiate among \nvulnerabilities has never before been possible.\n\n## Our Approach\n\nWe have refined the prioritization thresholds based on FIRST's recommendations and our own experience. Here's an overview:\n\n1. We **include CISA's Known Exploited Vulnerabilities**, giving priority to CVEs found in KEV.\n2. The **CVSS Threshold is set to 6.0**, representing the weighted average CVSS Score from [CVE Details](https://www.cvedetails.com/cvss-score-distribution.php).\n3. The **EPSS Threshold is set to 0.2**, focusing on vulnerabilities with higher relevance above this threshold.\n\nThis approach categorizes vulnerabilities into five priority levels, allowing you to allocate resources more effectively.\n\n| **Priority** | **Description** |\n|--------------|----------------------------------|\n| Priority 1+ | CVEs found in CISA's KEV |\n| Priority 1 | CVEs in the Upper Right Quadrant |\n| Priority 2 | CVEs in the Lower Right Quadrant |\n| Priority 3 | CVEs in the Upper Left Quadrant |\n| Priority 4 | CVEs in the Lower Left Quadrant |\n\n\nBelow is a modified version of FIRST's recommendation after applying our own approach.\n\n\n\n**Note:** You can define your own thresholds when running the tool to tailor the results \nto your organization's risk appetite.\n\n## Installation\n\n### Github \n```shell\ngit clone https://github.com/TURROKS/CVE_Prioritizer.git\ncd CVE_Prioritizer\npip install -r requirements.txt\n```\n\n### pip\n```shell\npip install --user cve_prioritizer\n```\n\n## Usage\n\nTo use CVE_Prioritizer effectively, follow these steps:\n\n1. Request your API keys to avoid public rate limits:\n - **NIST NVD:** Request [here](https://nvd.nist.gov/developers/request-an-api-key)\n - **VULNCHECK (Fast):** Register [here](https://vulncheck.com/register).\n - **Save APIs:** Use the `-sa` or `--set-api` option to save your API Keys in your `.env` file.\n2. Select your CVE Data source:\n - **NIST NVD:** Default.\n - **[NVD++](https://vulncheck.com/nvd2):** Use `-vc` or `--vulncheck`.\n - **VulnCheck KEV:** Use `-vck` or `vulnchek_kev` **(ONLY WORKS WITH NVD++)**.\n3. Choose Input Method:\n - **Single CVE:** Use the `-c` followed by the CVE ID.\n - **List of CVEs:** Use `-l` followed by a **comma-separated** list of CVEs.\n - **File with CVEs:** Use `-f` to import a file containing CVE IDs (one per line).\n4. Tailor the output according to your needs:\n - Use the `-v` or `--verbose` for detailed information.\n - Define custom thresholds with `--cvss` and/or `--epss` to align the results with your organization's\n risk appetite.\n - Define the number of concurrent threads with `-t` or `--threads` (default: 100).\n\n### Examples\n\n#### Single CVE\n```\npython3 cve_prioritizer.py -c CVE-2020-29127\n```\n\n\n\n#### List of CVEs\n\n```\npython3 cve_prioritizer.py -l CVE-2020-29127,CVE-2017-16885\n```\n\n\n\n#### File with CVEs\nYou can also provide a text file with a list of CVEs (one per line)\n\n```\npython3 cve_prioritizer.py -f ~\\Desktop\\CheckTheseCVEs.txt\n```\n\n\n\n### Outputs\n\nCVE_Prioritizer provides flexible output options to suit your preferences. By default, it provides a summary of results,\nincluding the CVE-ID and its priority. However, you can enable verbose mode to obtain additional information.\n\nHere are the available output options:\n\n**Summary Results (default):** Provides a concise summary, including the CVE-ID and its priority.\n\n\n\n**Verbose Mode:** Enables detailed output with the following information for each CVE:\n\n- CVE ID\n- Priority\n- EPSS Score\n- CVSS Base Score\n- CVSS Version\n- CVSS Severity\n- KEV Status (TRUE or FALSE)\n- Vendor\n- Product\n- CVSS Vector\n\n\n\n**CSV File**\n\nYou can save the results to a CSV file by using the `-o` or `--output` flags\n\n```\npython3 cve_prioritizer.py -f cve_list.txt -o ~/Desktop/prioritized.csv\n```\n\n\n\nThis outputs the verbose results independently of the terminal output that you use.\n\n#### Contributing\n\nPlease refer to [CONTRIBUTING.md](https://raw.githubusercontent.com/TURROKS/CVE_Prioritizer/main/docs/CONTRIBUTING.md) for guidelines\n\n#### License\n\nThis project is licensed under the BSD 3-Clause license - see the [LICENSE](https://raw.githubusercontent.com/TURROKS/CVE_Prioritizer/main/LICENSE) file for details.\n\n#### Contact\n\nFor questions or issues, please contact me at prioritizer@proton.me\n\nHappy Patching!\n\n[](https://ko-fi.com/K3K4KOFV4)\n\n#### NVD API Notice: \nPlease note that while this tool uses the NVD API, it is not endorsed or certified by the NVD.\n\n\n",
"bugtrack_url": null,
"license": null,
"summary": "Streamline vulnerability patching with CVSS, EPSS, Known Exploited Vulnerabilities and more.",
"version": "1.7.2",
"project_urls": {
"Homepage": "https://github.com/TURROKS/CVE_Prioritizer"
},
"split_keywords": [],
"urls": [
{
"comment_text": "",
"digests": {
"blake2b_256": "760ac87297e8ee9385618e5ce56e77ffd59e35be982d84d3fe460b6c9c2deccc",
"md5": "26ce617031c761f35fe220473032d069",
"sha256": "25ba261b72124b9a5ed453a28ac5cf1c26a007add155069b3a95f3dd6795efc3"
},
"downloads": -1,
"filename": "CVE_Prioritizer-1.7.2-py3-none-any.whl",
"has_sig": false,
"md5_digest": "26ce617031c761f35fe220473032d069",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": ">=3.6",
"size": 27170,
"upload_time": "2024-10-06T08:47:04",
"upload_time_iso_8601": "2024-10-06T08:47:04.713705Z",
"url": "https://files.pythonhosted.org/packages/76/0a/c87297e8ee9385618e5ce56e77ffd59e35be982d84d3fe460b6c9c2deccc/CVE_Prioritizer-1.7.2-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": "",
"digests": {
"blake2b_256": "382d59901352efe96403995802cc8975c239ebc329d5cd2f755632bd4a768541",
"md5": "2db4db3a311de0eceb067e18d1e74027",
"sha256": "69eed545d5c5f795983caf7b8bcdeb07fcef55ffa5dd5236e78d0b6ac4db2780"
},
"downloads": -1,
"filename": "CVE_Prioritizer-1.7.2.tar.gz",
"has_sig": false,
"md5_digest": "2db4db3a311de0eceb067e18d1e74027",
"packagetype": "sdist",
"python_version": "source",
"requires_python": ">=3.6",
"size": 14466,
"upload_time": "2024-10-06T08:47:08",
"upload_time_iso_8601": "2024-10-06T08:47:08.496930Z",
"url": "https://files.pythonhosted.org/packages/38/2d/59901352efe96403995802cc8975c239ebc329d5cd2f755632bd4a768541/CVE_Prioritizer-1.7.2.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2024-10-06 08:47:08",
"github": true,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"github_user": "TURROKS",
"github_project": "CVE_Prioritizer",
"travis_ci": false,
"coveralls": false,
"github_actions": false,
"requirements": [
{
"name": "click",
"specs": [
[
">=",
"8.0.3"
]
]
},
{
"name": "pandas",
"specs": [
[
">=",
"1.5.3"
]
]
},
{
"name": "python-dotenv",
"specs": [
[
">=",
"0.19.2"
]
]
},
{
"name": "requests",
"specs": [
[
">=",
"2.32.3"
]
]
},
{
"name": "termcolor",
"specs": [
[
">=",
"2.2.0"
]
]
}
],
"lcname": "cve-prioritizer"
}
