| Name | credentialdigger JSON |
| Version |
4.14.5
 JSON
JSON |
| download |
| home_page | None |
| Summary | Credential Digger |
| upload_time | 2025-02-17 09:00:46 |
| maintainer | None |
| docs_url | None |
| author | SAP SE |
| requires_python | <3.13,>3.8 |
| license | Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Definitions.
"License" shall mean the terms and conditions for use, reproduction,
and distribution as defined by Sections 1 through 9 of this document.
"Licensor" shall mean the copyright owner or entity authorized by
the copyright owner that is granting the License.
"Legal Entity" shall mean the union of the acting entity and all
other entities that control, are controlled by, or are under common
control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the
direction or management of such entity, whether by contract or
otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity
exercising permissions granted by this License.
"Source" form shall mean the preferred form for making modifications,
including but not limited to software source code, documentation
source, and configuration files.
"Object" form shall mean any form resulting from mechanical
transformation or translation of a Source form, including but
not limited to compiled object code, generated documentation,
and conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or
Object form, made available under the License, as indicated by a
copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
"Derivative Works" shall mean any work, whether in Source or Object
form, that is based on (or derived from) the Work and for which the
editorial revisions, annotations, elaborations, or other modifications
represent, as a whole, an original work of authorship. For the purposes
of this License, Derivative Works shall not include works that remain
separable from, or merely link (or bind by name) to the interfaces of,
the Work and Derivative Works thereof.
"Contribution" shall mean any work of authorship, including
the original version of the Work and any modifications or additions
to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner
or by an individual or Legal Entity authorized to submit on behalf of
the copyright owner. For the purposes of this definition, "submitted"
means any form of electronic, verbal, or written communication sent
to the Licensor or its representatives, including but not limited to
communication on electronic mailing lists, source code control systems,
and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but
excluding communication that is conspicuously marked or otherwise
designated in writing by the copyright owner as "Not a Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity
on behalf of whom a Contribution has been received by Licensor and
subsequently incorporated within the Work.
2. Grant of Copyright License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
copyright license to reproduce, prepare Derivative Works of,
publicly display, publicly perform, sublicense, and distribute the
Work and such Derivative Works in Source or Object form.
3. Grant of Patent License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made,
use, offer to sell, sell, import, and otherwise transfer the Work,
where such license applies only to those patent claims licensable
by such Contributor that are necessarily infringed by their
Contribution(s) alone or by combination of their Contribution(s)
with the Work to which such Contribution(s) was submitted. If You
institute patent litigation against any entity (including a
cross-claim or counterclaim in a lawsuit) alleging that the Work
or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses
granted to You under this License for that Work shall terminate
as of the date such litigation is filed.
4. Redistribution. You may reproduce and distribute copies of the
Work or Derivative Works thereof in any medium, with or without
modifications, and in Source or Object form, provided that You
meet the following conditions:
(a) You must give any other recipients of the Work or
Derivative Works a copy of this License; and
(b) You must cause any modified files to carry prominent notices
stating that You changed the files; and
(c) You must retain, in the Source form of any Derivative Works
that You distribute, all copyright, patent, trademark, and
attribution notices from the Source form of the Work,
excluding those notices that do not pertain to any part of
the Derivative Works; and
(d) If the Work includes a "NOTICE" text file as part of its
distribution, then any Derivative Works that You distribute must
include a readable copy of the attribution notices contained
within such NOTICE file, excluding those notices that do not
pertain to any part of the Derivative Works, in at least one
of the following places: within a NOTICE text file distributed
as part of the Derivative Works; within the Source form or
documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and
wherever such third-party notices normally appear. The contents
of the NOTICE file are for informational purposes only and
do not modify the License. You may add Your own attribution
notices within Derivative Works that You distribute, alongside
or as an addendum to the NOTICE text from the Work, provided
that such additional attribution notices cannot be construed
as modifying the License.
You may add Your own copyright statement to Your modifications and
may provide additional or different license terms and conditions
for use, reproduction, or distribution of Your modifications, or
for any such Derivative Works as a whole, provided Your use,
reproduction, and distribution of the Work otherwise complies with
the conditions stated in this License.
5. Submission of Contributions. Unless You explicitly state otherwise,
any Contribution intentionally submitted for inclusion in the Work
by You to the Licensor shall be under the terms and conditions of
this License, without any additional terms or conditions.
Notwithstanding the above, nothing herein shall supersede or modify
the terms of any separate license agreement you may have executed
with Licensor regarding such Contributions.
6. Trademarks. This License does not grant permission to use the trade
names, trademarks, service marks, or product names of the Licensor,
except as required for reasonable and customary use in describing the
origin of the Work and reproducing the content of the NOTICE file.
7. Disclaimer of Warranty. Unless required by applicable law or
agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
PARTICULAR PURPOSE. You are solely responsible for determining the
appropriateness of using or redistributing the Work and assume any
risks associated with Your exercise of permissions under this License.
8. Limitation of Liability. In no event and under no legal theory,
whether in tort (including negligence), contract, or otherwise,
unless required by applicable law (such as deliberate and grossly
negligent acts) or agreed to in writing, shall any Contributor be
liable to You for damages, including any direct, indirect, special,
incidental, or consequential damages of any character arising as a
result of this License or out of the use or inability to use the
Work (including but not limited to damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all
other commercial damages or losses), even if such Contributor
has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability. While redistributing
the Work or Derivative Works thereof, You may choose to offer,
and charge a fee for, acceptance of support, warranty, indemnity,
or other liability obligations and/or rights consistent with this
License. However, in accepting such obligations, You may act only
on Your own behalf and on Your sole responsibility, not on behalf
of any other Contributor, and only if You agree to indemnify,
defend, and hold each Contributor harmless for any liability
incurred by, or claims asserted against, such Contributor by reason
of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work.
To apply the Apache License to your work, attach the following
boilerplate notice, with the fields enclosed by brackets "[]"
replaced with your own identifying information. (Don't include
the brackets!) The text should be enclosed in the appropriate
comment syntax for the file format. We also recommend that a
file or class name and description of purpose be included on the
same "printed page" as the copyright notice for easier
identification within third-party archives.
Copyright 2020-21 SAP SE or an SAP affiliate company and credential-digger contributors
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
|
| keywords |
|
| VCS |
 |
| bugtrack_url |
|
| requirements |
Flask
flask_jwt_extended
GitPython
hyperscan
numpy
pandas
psycopg2-binary
PyGithub
python-dotenv
pyyaml
rich
srsly
tensorflow
tensorflow-text
tf-models-official
transformers
|
| Travis-CI |
No Travis.
|
| coveralls test coverage |
No coveralls.
|
[](https://api.reuse.software/info/github.com/SAP/credential-digger)



[](https://hub.docker.com/r/saposs/credentialdigger)
[](https://marketplace.visualstudio.com/items?itemName=SAPOSS.vs-code-extension-for-project-credential-digger)

# Credential Digger
Credential Digger is a GitHub scanning tool that identifies hardcoded credentials (Passwords, API Keys, Secret Keys, Tokens, personal information, etc), filtering the false positive data through machine learning models.
TLDR; watch the video ⬇️
[](https://www.youtube.com/watch?v=1qz8lYPrtMo)
- [Credential Digger](#credential-digger)
- [Why](#why)
- [Requirements](#requirements)
- [Download and Installation](#download-and-installation)
- [How to run](#how-to-run)
- [Add rules](#add-rules)
- [Scan a repository](#scan-a-repository)
- [Docker container](#docker-container)
- [Advanced Installation](#advanced-installation)
- [Build from source](#build-from-source)
- [External postgres database](#external-postgres-database)
- [How to update the project](#how-to-update-the-project)
- [Python library usage](#python-library-usage)
- [Add rules](#add-rules-1)
- [Scan a repository](#scan-a-repository-1)
- [CLI - Command Line Interface](#cli---command-line-interface)
- [Micosoft Visual Studio Plug-in](#Micosoft-Visual-Studio-Plugin)
- [pre-commit hook](#pre-commit-hook)
- [CI/CD Pipeline Intergation on Piper](#cicd-pipeline-intergation-on-piper)
- [Wiki](#wiki)
- [Contributing](#contributing)
- [How to obtain support](#how-to-obtain-support)
- [News](#news)
## Why
In data protection, one of the most critical threats is represented by hardcoded (or plaintext) credentials in open-source projects. Several tools are already available to detect leaks in open-source platforms, but the diversity of credentials (depending on multiple factors such as the programming language, code development conventions, or developers' personal habits) is a bottleneck for the effectiveness of these tools. Their lack of precision leads to a very high number of pieces of code incorrectly detected as leaked secrets. Data wrongly detected as a leak is called _false positive_ data, and compose the huge majority of the data detected by currently available tools.
The goal of Credential Digger is to reduce the amount of false positive data on the output of the scanning phase by leveraging machine learning models.
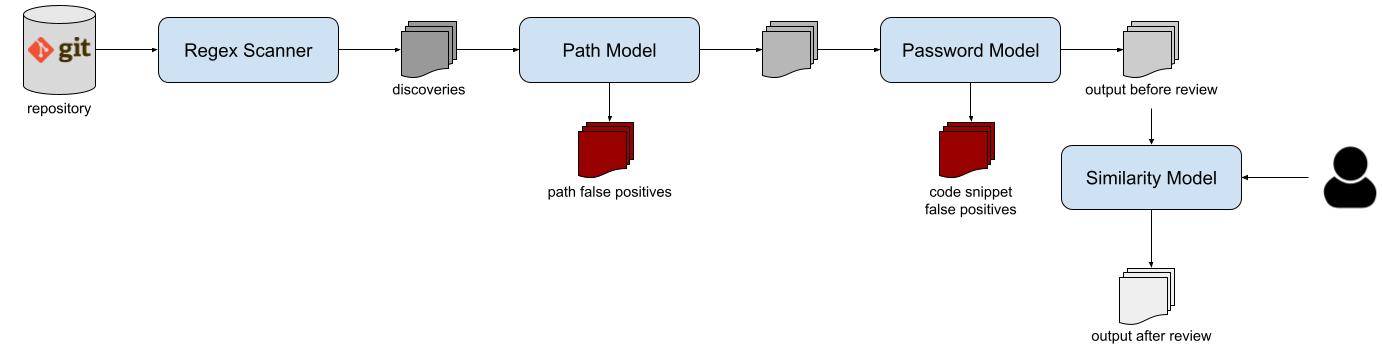
The tool supports several scan flavors: public and private repositories on
github and gitlab, pull requests, wiki pages, github organizations, local git repositories, local files and folders.
Please refer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for the complete documentation.
For the complete description of the approach of Credential Digger (versions <4.4), [you can read this publication](https://www.scitepress.org/Papers/2021/102381/102381.pdf).
```
@InProceedings {lrnto-icissp21,
author = {S. Lounici and M. Rosa and C. M. Negri and S. Trabelsi and M. Önen},
booktitle = {Proc. of the 8th The International Conference on Information Systems Security and Privacy (ICISSP)},
title = {Optimizing Leak Detection in Open-Source Platforms with Machine Learning Techniques},
month = {February},
day = {11-13},
year = {2021}
}
```
## Requirements
Credential Digger supports Python >= 3.8 and < 3.13, and works only with Linux and MacOS systems.
In case you don't meet these requirements, you may consider running a [Docker container](#docker) (that also includes a user interface).
## Download and Installation
First, you need to install some dependencies (namely, `build-essential` and `python3-dev`). No need to explicitely install hyperscan anymore.
```bash
sudo apt install -y build-essential python3-dev
```
Then, you can install Credential Digger module using `pip`.
```bash
pip install credentialdigger
```
> For ARM machines (e.g., new MacBooks), installation is possible [following this guide](https://github.com/SAP/credential-digger/wiki/MacOS-ARM-Installation)
## How to run
### Add rules
One of the core components of Credential Digger is the regular expression scanner. You can choose the regular expressions rules you want (just follow the template [here](https://github.com/SAP/credential-digger/blob/main/ui/backend/rules.yml)). We provide a list of patterns in the `rules.yml` file, that are included in the UI. The scanner supports rules of 4 different categories: `password`, `token`, `crypto_key`, and `other`.
**Before the very first scan, you need to add the rules that will be used by the scanner.** This step is only needed once.
```bash
credentialdigger add_rules --sqlite /path/to/data.db /path/to/rules.yaml
```
### Scan a repository
After adding the rules, you can scan a repository:
```bash
credentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db
```
Machine learning models are not mandatory, but highly recommended in order to reduce the manual effort of reviewing the result of a scan:
```bash
credentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db --models PathModel PasswordModel
```
As for the models, also the similarity feature is not mandatory, but highly recommended in order to reduce the manual effort while assessing the discoveries after a scan:
```bash
credentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db --similarity --models PathModel PasswordModel
```
## Docker container
To have a ready-to-use instance of Credential Digger, with a user interface, you can use a docker container.
This option requires the installation of [Docker](https://docs.docker.com/engine/install/) and [Docker Compose](https://docs.docker.com/compose/install/).
Credential Digger is published on [dockerhub](https://hub.docker.com/r/saposs/credentialdigger). You can pull the latest release
```bash
sudo docker pull saposs/credentialdigger
```
Or build and run containers with docker compose
```bash
git clone https://github.com/SAP/credential-digger.git
cd credential-digger
cp .env.sample .env
docker compose up --build
```
The UI is available at [http://localhost:5000/](http://localhost:5000/)
> It is preferrable to have at least 8 GB of RAM free when using docker containers
## Advanced Installation
Credential Digger is modular, and offers a wide choice of components and adaptations.
### Build from source
After installing the [dependencies](#install-dependencies) listed above, you can install Credential Digger as follows.
Configure a virtual environment for Python 3 (optional) and clone the main branch of the project:
```bash
virtualenv -p python3 ./venv
source ./venv/bin/activate
git clone https://github.com/SAP/credential-digger.git
cd credential-digger
```
Install the tool from source:
```bash
pip install .
```
Then, you can add the rules and scan a repository as described above.
### External postgres database
Another ready-to-use instance of Credential Digger with the UI, but using a dockerized postgres database instead of a local sqlite one:
```bash
git clone https://github.com/SAP/credential-digger.git
cd credential-digger
cp .env.sample .env
vim .env # set credentials for postgres
docker compose -f docker-compose.postgres.yml up --build
```
> **WARNING**: Differently from the sqlite version, here we need to configure the `.env` file with the credentials for postgres (by modifying `POSTGRES_USER`, `POSTGRES_PASSWORD` and `POSTGRES_DB`).
Most advanced users may also wish to use an external postgres database instead of the dockerized one we provide in our `docker-compose.postgres.yml`.
## How to update the project
If you are already running Credential Digger and you want to update it to a
newer version, you can
[refer to the wiki for the needed steps](https://github.com/SAP/credential-digger/wiki/How-to-update-Credential-Digger).
## Python library usage
When installing _credentialdigger_ from pip (or from source), you can instantiate the client and scan a repository.
Instantiate the client proper for the chosen database:
```python
# Using a Sqlite database
from credentialdigger import SqliteClient
c = SqliteClient(path='/path/to/data.db')
# Using a postgres database
from credentialdigger import PgClient
c = PgClient(dbname='my_db_name',
dbuser='my_user',
dbpassword='my_password',
dbhost='localhost_or_ip',
dbport=5432)
```
### Add rules
Add rules before launching your first scan.
```python
c.add_rules_from_file('/path/to/rules.yml')
```
### Scan a repository
```python
new_discoveries = c.scan(repo_url='https://github.com/user/repo',
models=['PathModel', 'PasswordModel'],
debug=True)
```
> **WARNING**: Make sure you add the rules before your first scan.
Please refer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for further information on the arguments.
## CLI - Command Line Interface
Credential Digger also offers a simple CLI to scan a repository. The CLI supports both sqlite and postgres databases. In case of postgres, you need either to export the credentials needed to connect to the database as environment variables or to setup a `.env` file. In case of sqlite, the path of the db must be passed as argument.
Refer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for all the supported commands and their usage.
## Micosoft Visual Studio Plugin
VS Code extension for project "Credential Digger" is a free IDE extension that let you detect secrets and credentials in your code before they get leaked! Like a spell checker, the extension scans your files using the Credential Digger and highlights the secrets as you write code, so you can fix them before the code is even committed.
The VS Code extension can be donwloaded from the [Microsoft VS Code Marketplace](https://marketplace.visualstudio.com/items?itemName=SAPOSS.vs-code-extension-for-project-credential-digger)

## pre-commit hook
Credential Digger can be used with the [pre-commit](https://pre-commit.com/) framework to scan staged files before each commit.
Please, refer to the [Wiki page of the pre-commit hook](https://github.com/SAP/credential-digger/wiki/pre-commit-hook) for further information on its installation and execution.
## CI/CD Pipeline Intergation on Piper (SAP Jenkins Library)

Credential Digger is intergrated with the continuous delivery CI/CD pipeline [Piper](https://www.project-piper.io/) in order to automate secrets scans for your Github projects and repositories.
In order to activate the Credential Diggger Step please refer to this [Credential Digger step documentation for Piper](https://www.project-piper.io/steps/credentialdiggerScan/)
## Wiki
For further information, please refer to the [Wiki](https://github.com/SAP/credential-digger/wiki)
## Contributing
We invite your participation to the project through issues and pull requests. Please refer to the [Contributing guidelines](https://github.com/SAP/credential-digger/blob/main/CONTRIBUTING.md) for how to contribute.
## How to obtain support
As a first step, we suggest to [read the wiki](https://github.com/SAP/credential-digger/wiki).
In case you don't find the answers you need, you can open an [issue](https://github.com/SAP/credential-digger/issues) or contact the [maintainers](https://github.com/SAP/credential-digger/blob/main/setup.py#L19).
## News
- [Credential Digger announcement](https://blogs.sap.com/2020/06/23/credential-digger-using-machine-learning-to-identify-hardcoded-credentials-in-github)
- [Credential Digger is now supporting Keras machine learning models](https://github.com/SAP/credential-digger/tree/keras_models)
- [Credential Digger approach has been published at ICISSP 2021 conference](https://www.scitepress.org/Papers/2021/102381/102381.pdf)
Raw data
{
"_id": null,
"home_page": null,
"name": "credentialdigger",
"maintainer": null,
"docs_url": null,
"requires_python": "<3.13,>3.8",
"maintainer_email": "Marco Rosa <marco.rosa@sap.com>, Slim Trabelsi <slim.trabelsi@sap.com>",
"keywords": null,
"author": "SAP SE",
"author_email": null,
"download_url": "https://files.pythonhosted.org/packages/b9/ca/03d3fe94d41db1ebd12396177be903f16a5a3a0c9d7a65e44278eaa6e609/credentialdigger-4.14.5.tar.gz",
"platform": null,
"description": "[](https://api.reuse.software/info/github.com/SAP/credential-digger)\n\n\n\n[](https://hub.docker.com/r/saposs/credentialdigger)\n[](https://marketplace.visualstudio.com/items?itemName=SAPOSS.vs-code-extension-for-project-credential-digger)\n\n\n\n\n# Credential Digger\n\nCredential Digger is a GitHub scanning tool that identifies hardcoded credentials (Passwords, API Keys, Secret Keys, Tokens, personal information, etc), filtering the false positive data through machine learning models.\n\nTLDR; watch the video \u2b07\ufe0f\n\n[](https://www.youtube.com/watch?v=1qz8lYPrtMo)\n\n\n\n- [Credential Digger](#credential-digger)\n - [Why](#why)\n - [Requirements](#requirements)\n - [Download and Installation](#download-and-installation)\n - [How to run](#how-to-run)\n - [Add rules](#add-rules)\n - [Scan a repository](#scan-a-repository)\n - [Docker container](#docker-container)\n - [Advanced Installation](#advanced-installation)\n - [Build from source](#build-from-source)\n - [External postgres database](#external-postgres-database)\n - [How to update the project](#how-to-update-the-project)\n - [Python library usage](#python-library-usage)\n - [Add rules](#add-rules-1)\n - [Scan a repository](#scan-a-repository-1)\n - [CLI - Command Line Interface](#cli---command-line-interface)\n - [Micosoft Visual Studio Plug-in](#Micosoft-Visual-Studio-Plugin)\n - [pre-commit hook](#pre-commit-hook)\n - [CI/CD Pipeline Intergation on Piper](#cicd-pipeline-intergation-on-piper)\n - [Wiki](#wiki)\n - [Contributing](#contributing)\n - [How to obtain support](#how-to-obtain-support)\n - [News](#news)\n\n## Why\nIn data protection, one of the most critical threats is represented by hardcoded (or plaintext) credentials in open-source projects. Several tools are already available to detect leaks in open-source platforms, but the diversity of credentials (depending on multiple factors such as the programming language, code development conventions, or developers' personal habits) is a bottleneck for the effectiveness of these tools. Their lack of precision leads to a very high number of pieces of code incorrectly detected as leaked secrets. Data wrongly detected as a leak is called _false positive_ data, and compose the huge majority of the data detected by currently available tools.\n\nThe goal of Credential Digger is to reduce the amount of false positive data on the output of the scanning phase by leveraging machine learning models.\n\n\n\n\nThe tool supports several scan flavors: public and private repositories on\ngithub and gitlab, pull requests, wiki pages, github organizations, local git repositories, local files and folders.\nPlease refer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for the complete documentation.\n\nFor the complete description of the approach of Credential Digger (versions <4.4), [you can read this publication](https://www.scitepress.org/Papers/2021/102381/102381.pdf).\n\n```\n@InProceedings {lrnto-icissp21,\n author = {S. Lounici and M. Rosa and C. M. Negri and S. Trabelsi and M. \u00d6nen},\n booktitle = {Proc. of the 8th The International Conference on Information Systems Security and Privacy (ICISSP)},\n title = {Optimizing Leak Detection in Open-Source Platforms with Machine Learning Techniques},\n month = {February},\n day = {11-13},\n year = {2021}\n}\n```\n\n## Requirements\n\nCredential Digger supports Python >= 3.8 and < 3.13, and works only with Linux and MacOS systems.\nIn case you don't meet these requirements, you may consider running a [Docker container](#docker) (that also includes a user interface).\n\n## Download and Installation\n\nFirst, you need to install some dependencies (namely, `build-essential` and `python3-dev`). No need to explicitely install hyperscan anymore.\n\n```bash\nsudo apt install -y build-essential python3-dev\n```\n\nThen, you can install Credential Digger module using `pip`.\n\n```bash\npip install credentialdigger\n```\n\n> For ARM machines (e.g., new MacBooks), installation is possible [following this guide](https://github.com/SAP/credential-digger/wiki/MacOS-ARM-Installation)\n\n\n## How to run\n\n### Add rules\n\nOne of the core components of Credential Digger is the regular expression scanner. You can choose the regular expressions rules you want (just follow the template [here](https://github.com/SAP/credential-digger/blob/main/ui/backend/rules.yml)). We provide a list of patterns in the `rules.yml` file, that are included in the UI. The scanner supports rules of 4 different categories: `password`, `token`, `crypto_key`, and `other`.\n\n**Before the very first scan, you need to add the rules that will be used by the scanner.** This step is only needed once.\n\n```bash\ncredentialdigger add_rules --sqlite /path/to/data.db /path/to/rules.yaml\n```\n\n### Scan a repository\n\nAfter adding the rules, you can scan a repository:\n\n```bash\ncredentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db\n```\n\nMachine learning models are not mandatory, but highly recommended in order to reduce the manual effort of reviewing the result of a scan:\n\n```bash\ncredentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db --models PathModel PasswordModel\n```\n\nAs for the models, also the similarity feature is not mandatory, but highly recommended in order to reduce the manual effort while assessing the discoveries after a scan:\n\n```bash\ncredentialdigger scan https://github.com/user/repo --sqlite /path/to/data.db --similarity --models PathModel PasswordModel\n```\n\n\n## Docker container\n\nTo have a ready-to-use instance of Credential Digger, with a user interface, you can use a docker container. \nThis option requires the installation of [Docker](https://docs.docker.com/engine/install/) and [Docker Compose](https://docs.docker.com/compose/install/).\n\nCredential Digger is published on [dockerhub](https://hub.docker.com/r/saposs/credentialdigger). You can pull the latest release\n\n```bash\nsudo docker pull saposs/credentialdigger\n```\n\nOr build and run containers with docker compose\n\n```bash\ngit clone https://github.com/SAP/credential-digger.git\ncd credential-digger\ncp .env.sample .env\ndocker compose up --build\n```\n\nThe UI is available at [http://localhost:5000/](http://localhost:5000/)\n\n> It is preferrable to have at least 8 GB of RAM free when using docker containers\n\n\n## Advanced Installation\n\nCredential Digger is modular, and offers a wide choice of components and adaptations.\n\n### Build from source\n\nAfter installing the [dependencies](#install-dependencies) listed above, you can install Credential Digger as follows.\n\nConfigure a virtual environment for Python 3 (optional) and clone the main branch of the project:\n\n```bash\nvirtualenv -p python3 ./venv\nsource ./venv/bin/activate\n\ngit clone https://github.com/SAP/credential-digger.git\ncd credential-digger\n```\n\nInstall the tool from source:\n\n```bash\npip install .\n```\n\nThen, you can add the rules and scan a repository as described above.\n\n### External postgres database\n\nAnother ready-to-use instance of Credential Digger with the UI, but using a dockerized postgres database instead of a local sqlite one:\n\n```bash\ngit clone https://github.com/SAP/credential-digger.git\ncd credential-digger\ncp .env.sample .env\nvim .env # set credentials for postgres\ndocker compose -f docker-compose.postgres.yml up --build\n```\n\n> **WARNING**: Differently from the sqlite version, here we need to configure the `.env` file with the credentials for postgres (by modifying `POSTGRES_USER`, `POSTGRES_PASSWORD` and `POSTGRES_DB`).\n\nMost advanced users may also wish to use an external postgres database instead of the dockerized one we provide in our `docker-compose.postgres.yml`.\n\n\n\n## How to update the project\nIf you are already running Credential Digger and you want to update it to a\nnewer version, you can \n[refer to the wiki for the needed steps](https://github.com/SAP/credential-digger/wiki/How-to-update-Credential-Digger).\n\n\n\n## Python library usage\n\nWhen installing _credentialdigger_ from pip (or from source), you can instantiate the client and scan a repository.\n\nInstantiate the client proper for the chosen database:\n\n```python\n# Using a Sqlite database\nfrom credentialdigger import SqliteClient\nc = SqliteClient(path='/path/to/data.db')\n\n# Using a postgres database\nfrom credentialdigger import PgClient\nc = PgClient(dbname='my_db_name',\n dbuser='my_user',\n dbpassword='my_password',\n dbhost='localhost_or_ip',\n dbport=5432)\n```\n\n### Add rules\n\nAdd rules before launching your first scan.\n\n```python\nc.add_rules_from_file('/path/to/rules.yml')\n```\n\n### Scan a repository\n\n```python\nnew_discoveries = c.scan(repo_url='https://github.com/user/repo',\n models=['PathModel', 'PasswordModel'],\n debug=True)\n```\n\n> **WARNING**: Make sure you add the rules before your first scan.\n\nPlease refer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for further information on the arguments.\n\n\n\n## CLI - Command Line Interface\n\nCredential Digger also offers a simple CLI to scan a repository. The CLI supports both sqlite and postgres databases. In case of postgres, you need either to export the credentials needed to connect to the database as environment variables or to setup a `.env` file. In case of sqlite, the path of the db must be passed as argument.\n\nRefer to the [Wiki](https://github.com/SAP/credential-digger/wiki) for all the supported commands and their usage.\n\n\n## Micosoft Visual Studio Plugin\n\nVS Code extension for project \"Credential Digger\" is a free IDE extension that let you detect secrets and credentials in your code before they get leaked! Like a spell checker, the extension scans your files using the Credential Digger and highlights the secrets as you write code, so you can fix them before the code is even committed.\n\nThe VS Code extension can be donwloaded from the [Microsoft VS Code Marketplace](https://marketplace.visualstudio.com/items?itemName=SAPOSS.vs-code-extension-for-project-credential-digger) \n\n\n\n\n## pre-commit hook\n\nCredential Digger can be used with the [pre-commit](https://pre-commit.com/) framework to scan staged files before each commit.\n\nPlease, refer to the [Wiki page of the pre-commit hook](https://github.com/SAP/credential-digger/wiki/pre-commit-hook) for further information on its installation and execution.\n\n\n## CI/CD Pipeline Intergation on Piper (SAP Jenkins Library)\n\n\n\nCredential Digger is intergrated with the continuous delivery CI/CD pipeline [Piper](https://www.project-piper.io/) in order to automate secrets scans for your Github projects and repositories.\nIn order to activate the Credential Diggger Step please refer to this [Credential Digger step documentation for Piper](https://www.project-piper.io/steps/credentialdiggerScan/)\n\n\n## Wiki\n\nFor further information, please refer to the [Wiki](https://github.com/SAP/credential-digger/wiki)\n\n\n## Contributing\n\nWe invite your participation to the project through issues and pull requests. Please refer to the [Contributing guidelines](https://github.com/SAP/credential-digger/blob/main/CONTRIBUTING.md) for how to contribute.\n\n\n\n## How to obtain support\n\nAs a first step, we suggest to [read the wiki](https://github.com/SAP/credential-digger/wiki).\nIn case you don't find the answers you need, you can open an [issue](https://github.com/SAP/credential-digger/issues) or contact the [maintainers](https://github.com/SAP/credential-digger/blob/main/setup.py#L19).\n\n\n\n## News\n\n- [Credential Digger announcement](https://blogs.sap.com/2020/06/23/credential-digger-using-machine-learning-to-identify-hardcoded-credentials-in-github)\n- [Credential Digger is now supporting Keras machine learning models](https://github.com/SAP/credential-digger/tree/keras_models)\n- [Credential Digger approach has been published at ICISSP 2021 conference](https://www.scitepress.org/Papers/2021/102381/102381.pdf)\n",
"bugtrack_url": null,
"license": "Apache License\n Version 2.0, January 2004\n http://www.apache.org/licenses/\n \n TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION\n \n 1. Definitions.\n \n \"License\" shall mean the terms and conditions for use, reproduction,\n and distribution as defined by Sections 1 through 9 of this document.\n \n \"Licensor\" shall mean the copyright owner or entity authorized by\n the copyright owner that is granting the License.\n \n \"Legal Entity\" shall mean the union of the acting entity and all\n other entities that control, are controlled by, or are under common\n control with that entity. For the purposes of this definition,\n \"control\" means (i) the power, direct or indirect, to cause the\n direction or management of such entity, whether by contract or\n otherwise, or (ii) ownership of fifty percent (50%) or more of the\n outstanding shares, or (iii) beneficial ownership of such entity.\n \n \"You\" (or \"Your\") shall mean an individual or Legal Entity\n exercising permissions granted by this License.\n \n \"Source\" form shall mean the preferred form for making modifications,\n including but not limited to software source code, documentation\n source, and configuration files.\n \n \"Object\" form shall mean any form resulting from mechanical\n transformation or translation of a Source form, including but\n not limited to compiled object code, generated documentation,\n and conversions to other media types.\n \n \"Work\" shall mean the work of authorship, whether in Source or\n Object form, made available under the License, as indicated by a\n copyright notice that is included in or attached to the work\n (an example is provided in the Appendix below).\n \n \"Derivative Works\" shall mean any work, whether in Source or Object\n form, that is based on (or derived from) the Work and for which the\n editorial revisions, annotations, elaborations, or other modifications\n represent, as a whole, an original work of authorship. For the purposes\n of this License, Derivative Works shall not include works that remain\n separable from, or merely link (or bind by name) to the interfaces of,\n the Work and Derivative Works thereof.\n \n \"Contribution\" shall mean any work of authorship, including\n the original version of the Work and any modifications or additions\n to that Work or Derivative Works thereof, that is intentionally\n submitted to Licensor for inclusion in the Work by the copyright owner\n or by an individual or Legal Entity authorized to submit on behalf of\n the copyright owner. For the purposes of this definition, \"submitted\"\n means any form of electronic, verbal, or written communication sent\n to the Licensor or its representatives, including but not limited to\n communication on electronic mailing lists, source code control systems,\n and issue tracking systems that are managed by, or on behalf of, the\n Licensor for the purpose of discussing and improving the Work, but\n excluding communication that is conspicuously marked or otherwise\n designated in writing by the copyright owner as \"Not a Contribution.\"\n \n \"Contributor\" shall mean Licensor and any individual or Legal Entity\n on behalf of whom a Contribution has been received by Licensor and\n subsequently incorporated within the Work.\n \n 2. Grant of Copyright License. Subject to the terms and conditions of\n this License, each Contributor hereby grants to You a perpetual,\n worldwide, non-exclusive, no-charge, royalty-free, irrevocable\n copyright license to reproduce, prepare Derivative Works of,\n publicly display, publicly perform, sublicense, and distribute the\n Work and such Derivative Works in Source or Object form.\n \n 3. Grant of Patent License. Subject to the terms and conditions of\n this License, each Contributor hereby grants to You a perpetual,\n worldwide, non-exclusive, no-charge, royalty-free, irrevocable\n (except as stated in this section) patent license to make, have made,\n use, offer to sell, sell, import, and otherwise transfer the Work,\n where such license applies only to those patent claims licensable\n by such Contributor that are necessarily infringed by their\n Contribution(s) alone or by combination of their Contribution(s)\n with the Work to which such Contribution(s) was submitted. If You\n institute patent litigation against any entity (including a\n cross-claim or counterclaim in a lawsuit) alleging that the Work\n or a Contribution incorporated within the Work constitutes direct\n or contributory patent infringement, then any patent licenses\n granted to You under this License for that Work shall terminate\n as of the date such litigation is filed.\n \n 4. Redistribution. You may reproduce and distribute copies of the\n Work or Derivative Works thereof in any medium, with or without\n modifications, and in Source or Object form, provided that You\n meet the following conditions:\n \n (a) You must give any other recipients of the Work or\n Derivative Works a copy of this License; and\n \n (b) You must cause any modified files to carry prominent notices\n stating that You changed the files; and\n \n (c) You must retain, in the Source form of any Derivative Works\n that You distribute, all copyright, patent, trademark, and\n attribution notices from the Source form of the Work,\n excluding those notices that do not pertain to any part of\n the Derivative Works; and\n \n (d) If the Work includes a \"NOTICE\" text file as part of its\n distribution, then any Derivative Works that You distribute must\n include a readable copy of the attribution notices contained\n within such NOTICE file, excluding those notices that do not\n pertain to any part of the Derivative Works, in at least one\n of the following places: within a NOTICE text file distributed\n as part of the Derivative Works; within the Source form or\n documentation, if provided along with the Derivative Works; or,\n within a display generated by the Derivative Works, if and\n wherever such third-party notices normally appear. The contents\n of the NOTICE file are for informational purposes only and\n do not modify the License. You may add Your own attribution\n notices within Derivative Works that You distribute, alongside\n or as an addendum to the NOTICE text from the Work, provided\n that such additional attribution notices cannot be construed\n as modifying the License.\n \n You may add Your own copyright statement to Your modifications and\n may provide additional or different license terms and conditions\n for use, reproduction, or distribution of Your modifications, or\n for any such Derivative Works as a whole, provided Your use,\n reproduction, and distribution of the Work otherwise complies with\n the conditions stated in this License.\n \n 5. Submission of Contributions. Unless You explicitly state otherwise,\n any Contribution intentionally submitted for inclusion in the Work\n by You to the Licensor shall be under the terms and conditions of\n this License, without any additional terms or conditions.\n Notwithstanding the above, nothing herein shall supersede or modify\n the terms of any separate license agreement you may have executed\n with Licensor regarding such Contributions.\n \n 6. Trademarks. This License does not grant permission to use the trade\n names, trademarks, service marks, or product names of the Licensor,\n except as required for reasonable and customary use in describing the\n origin of the Work and reproducing the content of the NOTICE file.\n \n 7. Disclaimer of Warranty. Unless required by applicable law or\n agreed to in writing, Licensor provides the Work (and each\n Contributor provides its Contributions) on an \"AS IS\" BASIS,\n WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or\n implied, including, without limitation, any warranties or conditions\n of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A\n PARTICULAR PURPOSE. You are solely responsible for determining the\n appropriateness of using or redistributing the Work and assume any\n risks associated with Your exercise of permissions under this License.\n \n 8. Limitation of Liability. In no event and under no legal theory,\n whether in tort (including negligence), contract, or otherwise,\n unless required by applicable law (such as deliberate and grossly\n negligent acts) or agreed to in writing, shall any Contributor be\n liable to You for damages, including any direct, indirect, special,\n incidental, or consequential damages of any character arising as a\n result of this License or out of the use or inability to use the\n Work (including but not limited to damages for loss of goodwill,\n work stoppage, computer failure or malfunction, or any and all\n other commercial damages or losses), even if such Contributor\n has been advised of the possibility of such damages.\n \n 9. Accepting Warranty or Additional Liability. While redistributing\n the Work or Derivative Works thereof, You may choose to offer,\n and charge a fee for, acceptance of support, warranty, indemnity,\n or other liability obligations and/or rights consistent with this\n License. However, in accepting such obligations, You may act only\n on Your own behalf and on Your sole responsibility, not on behalf\n of any other Contributor, and only if You agree to indemnify,\n defend, and hold each Contributor harmless for any liability\n incurred by, or claims asserted against, such Contributor by reason\n of your accepting any such warranty or additional liability.\n \n END OF TERMS AND CONDITIONS\n \n APPENDIX: How to apply the Apache License to your work.\n \n To apply the Apache License to your work, attach the following\n boilerplate notice, with the fields enclosed by brackets \"[]\"\n replaced with your own identifying information. (Don't include\n the brackets!) The text should be enclosed in the appropriate\n comment syntax for the file format. We also recommend that a\n file or class name and description of purpose be included on the\n same \"printed page\" as the copyright notice for easier\n identification within third-party archives.\n \n Copyright 2020-21 SAP SE or an SAP affiliate company and credential-digger contributors\n \n Licensed under the Apache License, Version 2.0 (the \"License\");\n you may not use this file except in compliance with the License.\n You may obtain a copy of the License at\n \n http://www.apache.org/licenses/LICENSE-2.0\n \n Unless required by applicable law or agreed to in writing, software\n distributed under the License is distributed on an \"AS IS\" BASIS,\n WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.\n See the License for the specific language governing permissions and\n limitations under the License.\n ",
"summary": "Credential Digger",
"version": "4.14.5",
"project_urls": {
"Documentation": "https://github.com/SAP/credential-digger/wiki",
"Homepage": "https://github.com/sap/credential-digger",
"Issues": "https://github.com/SAP/credential-digger/issues",
"Repository": "https://github.com/sap/credential-digger.git"
},
"split_keywords": [],
"urls": [
{
"comment_text": null,
"digests": {
"blake2b_256": "1a6e6268c3bd06307aa54fc5ae7968ec1e302859e25d202675b38469bf644538",
"md5": "06fa60b1d8785028ef06263e846702dc",
"sha256": "28b04e574f077595484619f77738341f3034b6118b3f2a71e26c36f296a38037"
},
"downloads": -1,
"filename": "credentialdigger-4.14.5-py3-none-any.whl",
"has_sig": false,
"md5_digest": "06fa60b1d8785028ef06263e846702dc",
"packagetype": "bdist_wheel",
"python_version": "py3",
"requires_python": "<3.13,>3.8",
"size": 69154,
"upload_time": "2025-02-17T09:00:44",
"upload_time_iso_8601": "2025-02-17T09:00:44.698988Z",
"url": "https://files.pythonhosted.org/packages/1a/6e/6268c3bd06307aa54fc5ae7968ec1e302859e25d202675b38469bf644538/credentialdigger-4.14.5-py3-none-any.whl",
"yanked": false,
"yanked_reason": null
},
{
"comment_text": null,
"digests": {
"blake2b_256": "b9ca03d3fe94d41db1ebd12396177be903f16a5a3a0c9d7a65e44278eaa6e609",
"md5": "0fae92671a513d7abcfcac8e5e38acbf",
"sha256": "aa1b3e2fc838b16d466b1f26ca6358c76dc523754186ef563978276f4a832d37"
},
"downloads": -1,
"filename": "credentialdigger-4.14.5.tar.gz",
"has_sig": false,
"md5_digest": "0fae92671a513d7abcfcac8e5e38acbf",
"packagetype": "sdist",
"python_version": "source",
"requires_python": "<3.13,>3.8",
"size": 54038,
"upload_time": "2025-02-17T09:00:46",
"upload_time_iso_8601": "2025-02-17T09:00:46.355859Z",
"url": "https://files.pythonhosted.org/packages/b9/ca/03d3fe94d41db1ebd12396177be903f16a5a3a0c9d7a65e44278eaa6e609/credentialdigger-4.14.5.tar.gz",
"yanked": false,
"yanked_reason": null
}
],
"upload_time": "2025-02-17 09:00:46",
"github": true,
"gitlab": false,
"bitbucket": false,
"codeberg": false,
"github_user": "SAP",
"github_project": "credential-digger",
"travis_ci": false,
"coveralls": false,
"github_actions": true,
"requirements": [
{
"name": "Flask",
"specs": []
},
{
"name": "flask_jwt_extended",
"specs": []
},
{
"name": "GitPython",
"specs": []
},
{
"name": "hyperscan",
"specs": [
[
"==",
"0.7.8"
]
]
},
{
"name": "numpy",
"specs": []
},
{
"name": "pandas",
"specs": []
},
{
"name": "psycopg2-binary",
"specs": []
},
{
"name": "PyGithub",
"specs": []
},
{
"name": "python-dotenv",
"specs": []
},
{
"name": "pyyaml",
"specs": []
},
{
"name": "rich",
"specs": [
[
"~=",
"13.9"
]
]
},
{
"name": "srsly",
"specs": [
[
">=",
"2.4.0"
]
]
},
{
"name": "tensorflow",
"specs": [
[
"==",
"2.18.0"
]
]
},
{
"name": "tensorflow-text",
"specs": [
[
"==",
"2.18.1"
]
]
},
{
"name": "tf-models-official",
"specs": []
},
{
"name": "transformers",
"specs": []
}
],
"lcname": "credentialdigger"
}
